Collect
Combine all your security data in one place, including SIEM logs, endpoint telemetry, threat intelligence, pen test findings and much more.
Strengthen your security posture and stop cyber attacks from a single easy-to-use platform.
Combine all your security data in one place, including SIEM logs, endpoint telemetry, threat intelligence, pen test findings and much more.
Get instant alerts to new threats affecting your business, backed by a 24/7 team of expert security analysts.
Quickly stop cyber attacks with automated blocking, host isolation and step-by-step remediation advice.
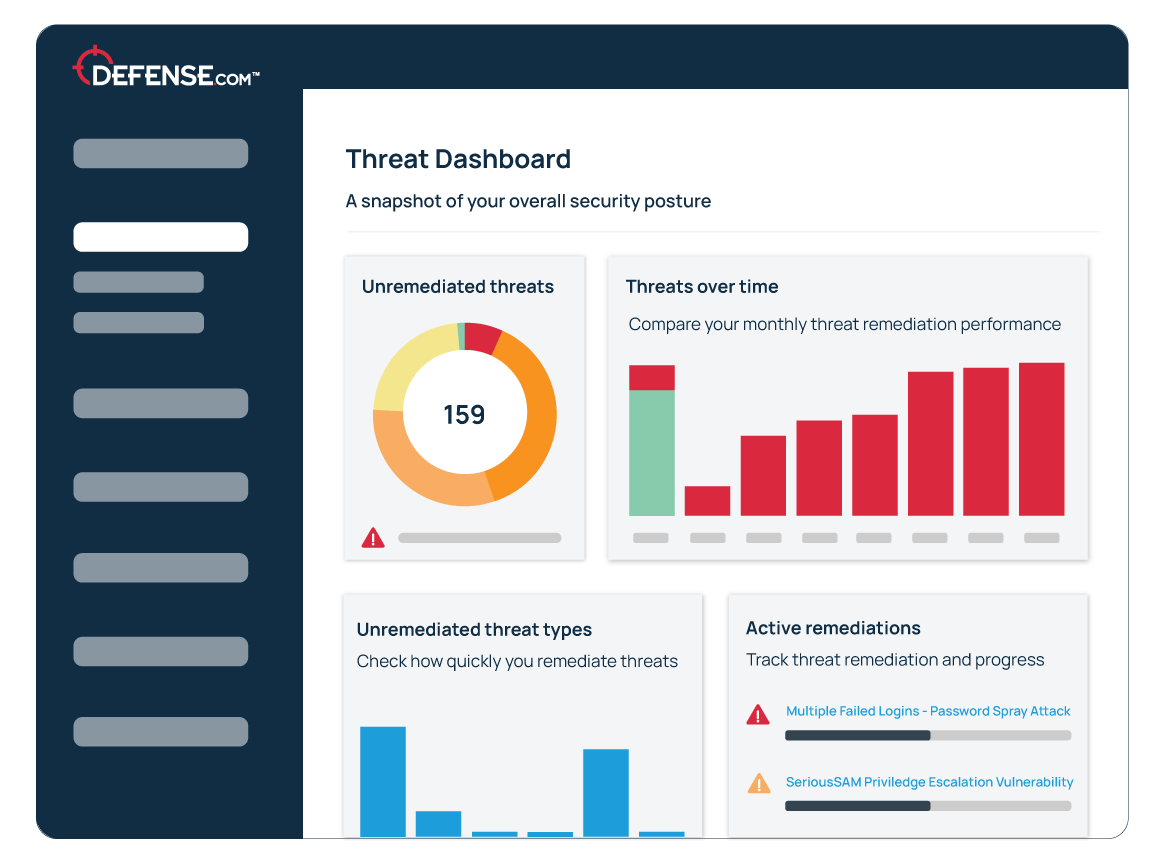
Ingest security logs and events from any source to detect malicious activity across your whole attack surface.
Defense.com can collect data from any third party vendor device, endpoint, cloud platform or application that can provide security value.
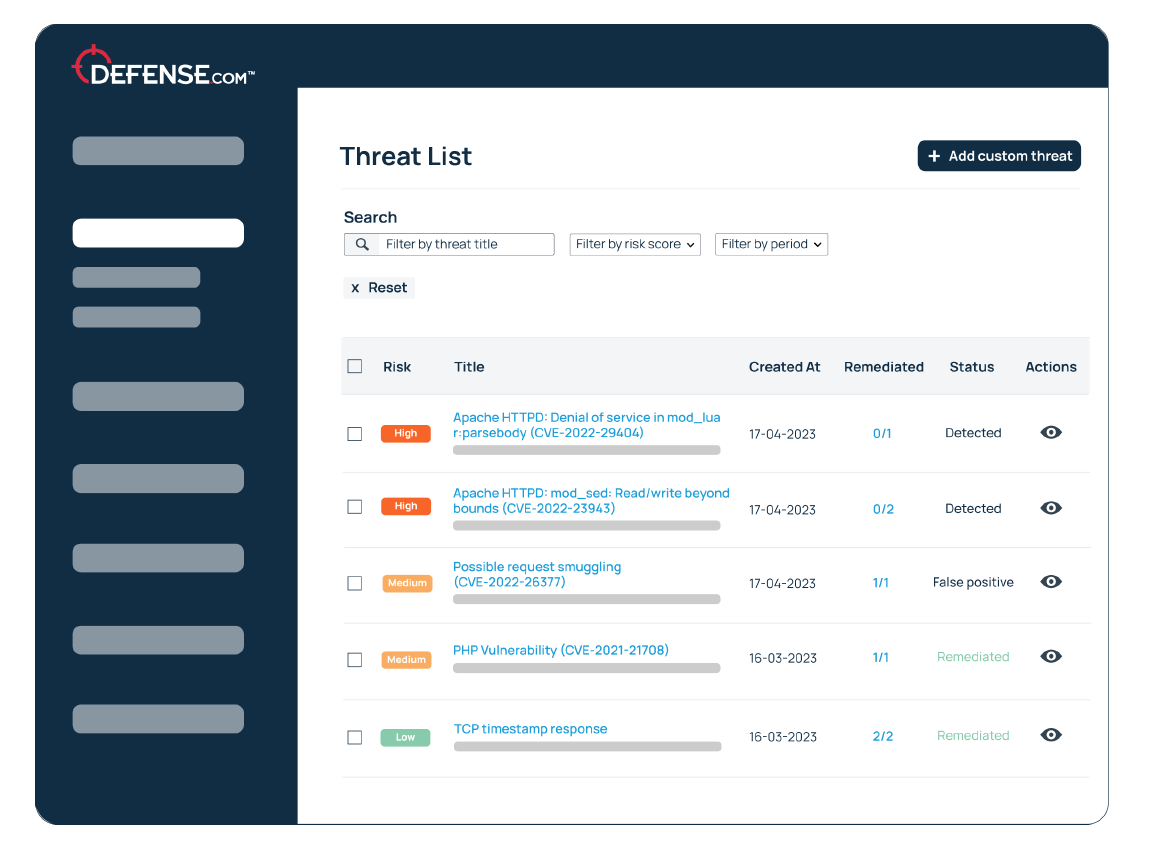
Get instant alerts to new threats and vulnerabilities affecting your business, all in one place.
Each alert is prioritised based on criticality, so you can focus on the most important issues first and use your resources more effectively.
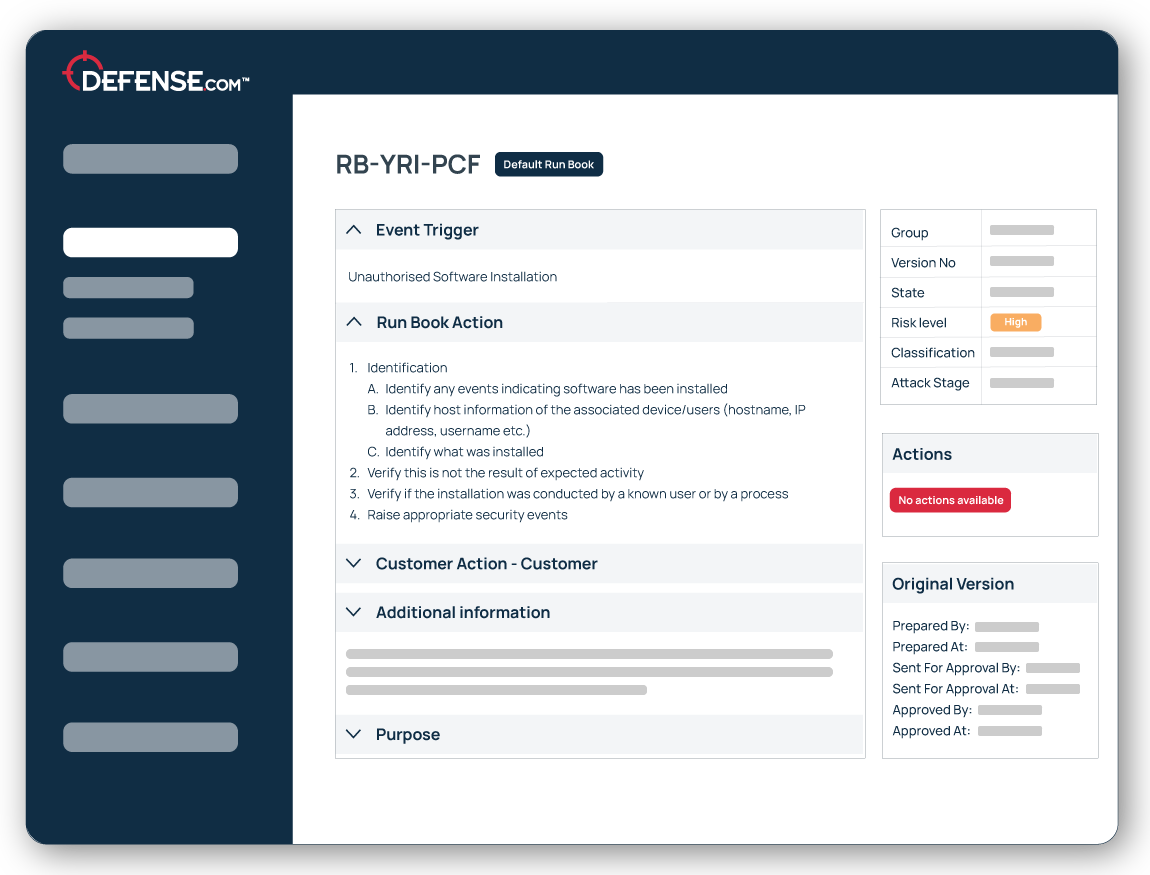
Quickly stop attacks and limit lateral movement with endpoint isolation and automated blocking.
Detailed runbooks and step-by-step remediation advice helps you respond to security incidents faster and stop breaches.
Detect and respond to cyber threats from a single SaaS-based platform.
Defend against advanced threats including ransomware and zero-days.
Identify and stop early-stage attacks before they turn into breaches.
Collect data from all your existing third party security investments.
Know exactly where to focus your time and resources, and how to remediate threats.
Take action quickly with host isolation and automated blocking.
Defense.com XDR has everything you need to detect threats and stop cyber attacks.
Cyber security can't be solved by one technology alone. Quickly improve more areas of your security posture with these additional features included in Defense.com™.

Defense.com XDR is easy to use on its own, but if you’d prefer to outsource your security operations, we can help.
Our managed security services take the pressure off your internal team and help you prevent breaches. Expert SOC analysts will monitor your environment 24/7 and raise threats to your attention, so you can focus on other tasks.
Learn moreGet your free 28-day trial of Defense.com with full access to all features. No credit card required.
XDR stands for eXtended Detection and Response. It is a modern approach to cyber security operations that enables organisations to identify, correlate, investigate and respond to threats from multiple sources with a single solution.
Here’s how Gartner defines XDR:
“Extended detection and response (XDR) delivers security incident detection and automated response capabilities for security infrastructure. XDR integrates threat intelligence and telemetry data from multiple sources with security analytics to provide contextualization and correlation of security alerts. XDR must include native sensors, and can be delivered on-premises or as a SaaS offering. Typically, it is deployed by organizations with smaller security teams.”
Endpoint Detection and Response (EDR) is solely focused on identifying and responding to threats at an endpoint level. XDR takes this further by detecting threats across your entire attack surface and correlating them into a single solution. This could include data from the following sources:
XDR solutions help you to triage and remediate security events more effectively.
The best XDR software solutions on the market collect security telemetry from multiple sources, so you can detect and respond to cyber threats across your entire attack surface.
XDR software can be very complex to configure, deploy and manage, which has traditionally led to it being inaccessible to small and medium sized businesses. Defense.com was built specifically to address this challenge, giving businesses with limited or no security resources enterprise-grade security without the enterprise complexity or price tag.
Many XDR solutions on the market also only work with native tools, leading to the disadvantages of vendor lock-in. Defense.com can collect data from any native or third party source, which means you don’t have to rip and replace your existing security technologies or stay tied to a single vendor.