Threat Recon
Scan your business domain(s) and see your external attack surface through the eyes of a hacker. Uncover hidden cyber risks and act on them before they are exploited.
Read more about threat recon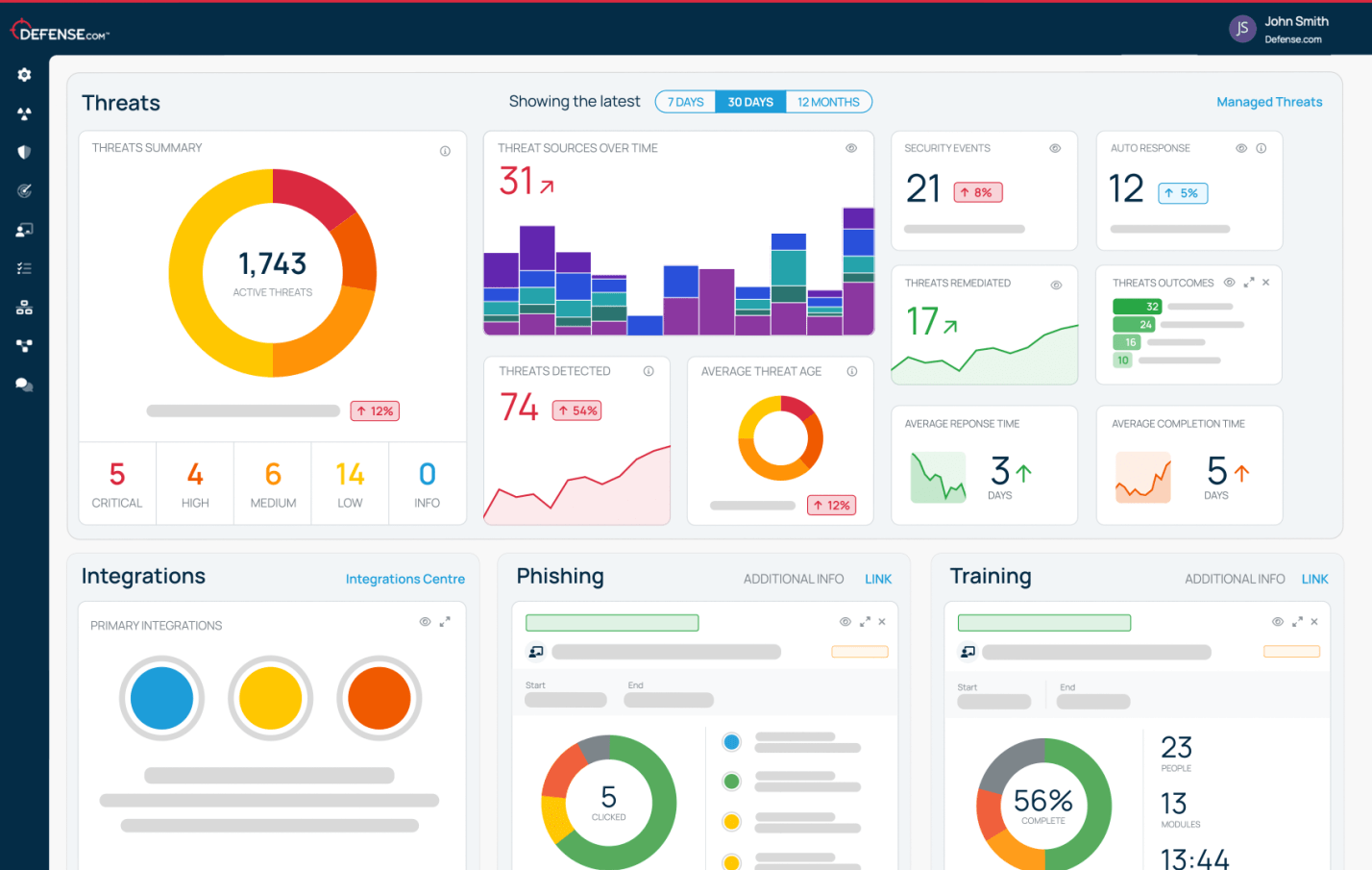




























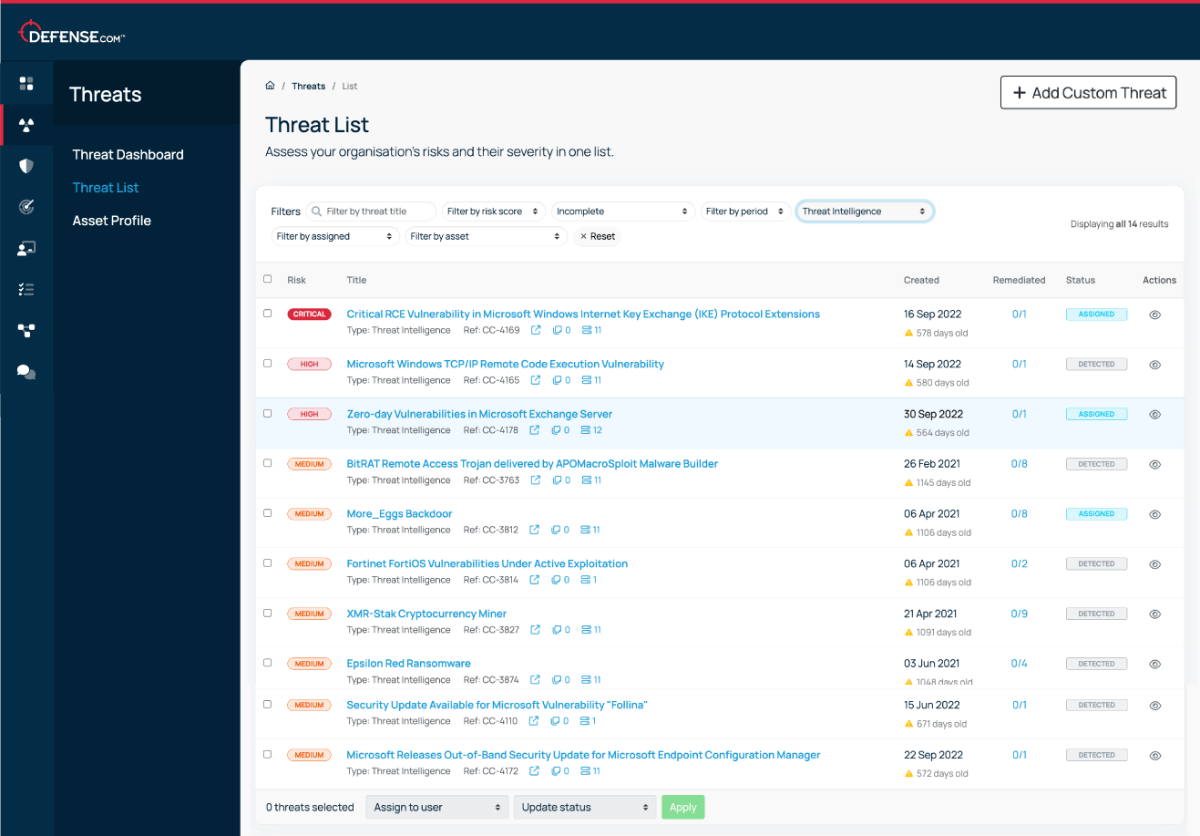
Identify and manage cyber threats from your whole environment.
Modern cyber threats are evolving and extend past just endpoints. That’s why it’s important to monitor your entire attack surface for suspicious activity.
Defense.com is an XDR platform that contains everything you need to detect and respond to cyber threats across all areas of your network, without the enterprise price tag or complexity.
Find out more

24/7 fully managed threat detection.
Defense.com Managed SIEM alleviates the pressure on your IT team by monitoring your environment 24/7 for cyber threats.
Our in-house Service Operations Center (SOC) analysts will become an extension of your team, proactively looking for malicious activity in your network and raising security alerts to your attention.
Find out more
Strengthen your security and free up your team with a 24/7 fully managed service.
Defense.com MDR is a fully managed, 24/7 threat detection and response service. Our security analysts proactively detect, investigate, and respond to threats, minimising the impact of cyber attacks on your business.
Find out moreCyber security can't be solved by one technology alone. Quickly improve more areas of your security posture with these additional features included in Defense.com™.
Whether you’re interested in finding out more about our XDR platform or managed services, our team will be happy to help.
Get actionable cyber security advice and insights straight to your inbox.