Over 8,000 CVEs are published every quarter
Track your assets and identify threats
Your assets define your attack surface, therefore it’s essential to understand how they could become targets.
New security vulnerabilities are discovered and disclosed every day, so intelligent asset tracking software should be a key part of your security controls to help with:
- Risk management
- Managing legacy systems
- Patch management
- Revealing shadow IT
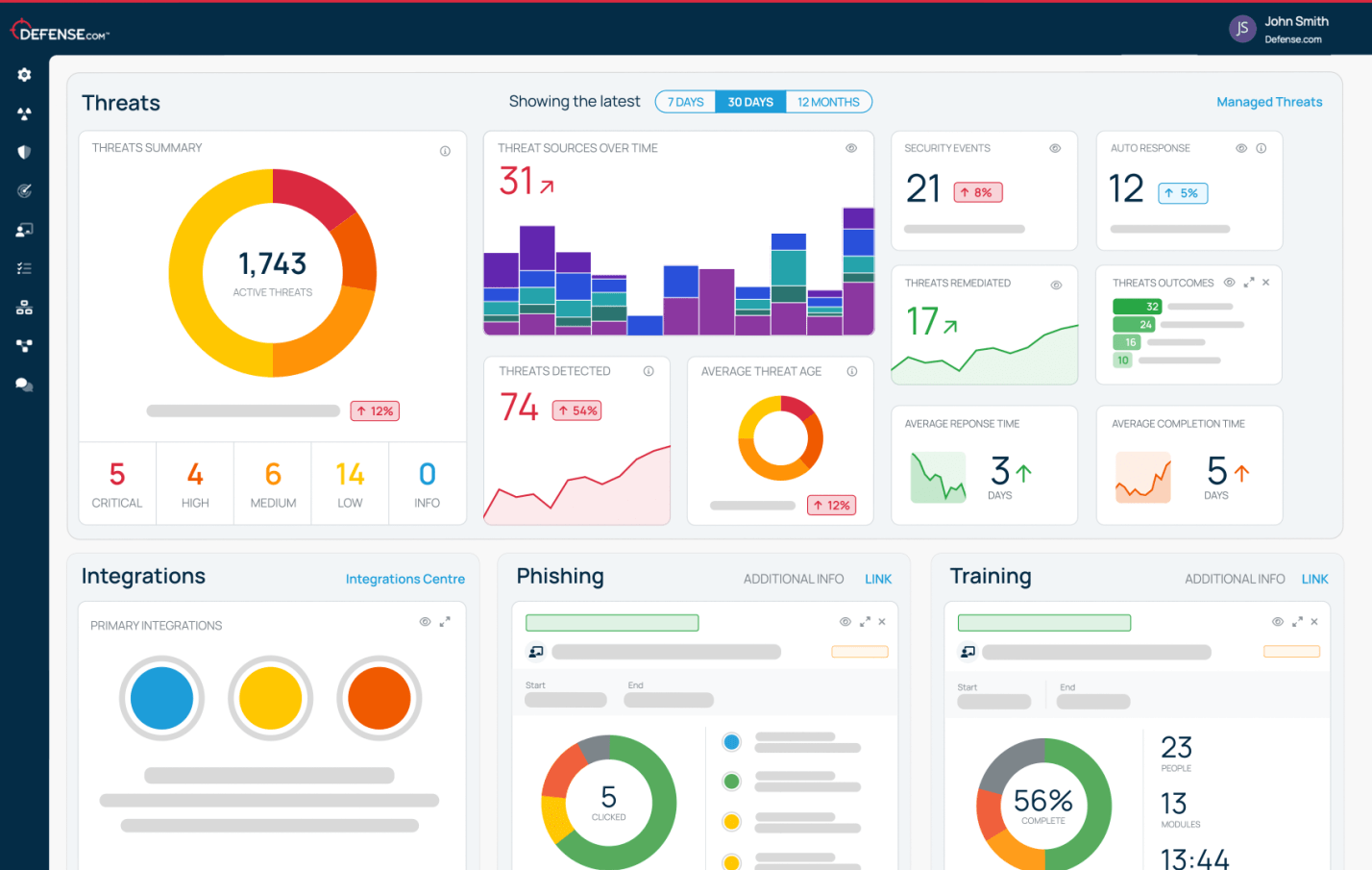
The easy-to-use Asset Profile feature in Defense.com™ maps threats directly to your unique list of hardware and operating systems, making it simple to gather, prioritize and action threat intelligence data.
Uncover security threats
Get tailored threat intelligence data and reveal hidden security risks based on the assets tracked within your company, so you can stay ahead of cyber threats.
Easy management tools
Keep your Asset Profile up-to-date with simple tools to add, edit, remove and label all operating systems, products and devices used across your organization.
Assign assets to users
Designate assets to specific people to easily keep track of what operating systems, software and hardware belong to which users.
Remediate threats quicker
Relevant threats affecting your assets are automatically created in your Threat Dashboard, allowing you to track and manage remediations with ease.
Effective security defenses
The easy-to-use Asset Profile in Defense.com™ can help you:
- Track operating systems, software, and hardware assets across your company
- Easily keep asset registers up to date
- Align cyber threats to assets for faster remediation
- Uncover hidden threats, boosting risk management
Get started on your security today
Start tracking your assets, managing threats and prioritizing remediations with a free trial of Defense.com™. Find out why security pros love our powerful all-in-one SaaS platform.
Try for freeHere’s what our customers say about us
Protecting the world’s leading brands
Asset profile FAQs
Asset tracking is the methodical and systemized recording of all operating systems, software, hardware and devices used in your organization. By having an easy-to-manage record of your asset estate, you get an informed and joined-up approach to managing your cyber threats.
Defense.com™’s Asset Profile is delivered as part of our all-in-one SaaS platform. The built-in asset tracking feature maps threat intel directly to your assets, revealing hidden security risks by letting you know what other vulnerable assets you have.
Asset tracking creates a smart list of all operating systems, software, hardware and devices that your company uses. Auto-complete fields make it faster and easier to add assets to the register, and engaging users to add their own also reveals shadow IT.
Asset trackers are most valuable when the intel they provide is used holistically to give whole-business benefit. In the case of Defense.com™, the Asset Profile feature improves vulnerability management and gives a joined-up approach that really boosts your security defenses.
Find out more about Defense.com™ packages