
Getting Started with Compliance
A complete guide to getting started with compliance including which cybersecurity and data protection standards…




Mikey Anderson
Product Marketing Manager
08th August 2023
In today's world, cyberattacks are inevitable. This makes it essential for organisations of all sizes to maintain a robust security posture and mitigate cyber risks.
With that in mind, regular risk assessments should be a key component of any cyber security strategy. By identifying, prioritising and managing cyber risks in a structured way, organisations can protect information and defend against cyber attacks more effectively. A defined cyber risk management strategy is also essential for demonstrating compliance with information security standards and regulatory bodies.
In this post, we’ll take a deep dive into how to perform a cyber risk assessment and what your organisation should keep in mind when completing them.
Cyber risk management should be a bespoke process, as every organisation is unique in terms of its attack surface and risk posture. By ensuring that your methodology is tailored to your specific cyber security requirements, you’ll be able to manage your risks effectively and ensure the most effective use of your resources.
Here are a few examples of common compliance standards, frameworks and regulations that help organisations to identify and reduce risk:
Depending on your industry, your organisation may already have a legal or compliance requirement to define and manage cyber risks in a particular way. For example, organisations that process or manage cardholder data will need to comply with PCI DSS, which has specific requirements for managing various types of cyber risk.
In any case, adopting a structured and tailored approach to risk assessments will make it easier to define and implement mitigating security controls, as you will be using a consistent and repeatable assessment process.
The first step in any cyber risk assessment should be to identify what is to be included in the scope of the assessment. This can be challenging if your organisation has a complex environment, however its crucial to ensure that all areas have been considered.
Here are some of the targets of the assessment that should be included:
A good place to start is by identifying, mapping and cataloguing all of the devices in your environment where information is stored, processed and/or transmitted. This could include servers, laptops, mobile devices, routers, modems, switches and any other internet-connected devices. One way to make this easier is to maintain a list of all assets in your organisation which will assist you in completing a risk assessment quickly, thoroughly and easily on a frequent basis.
Once you have identified your assets, it’s also important to also identify the locations where your business processes and stores data (this is especially important to ensure the Data Protection Act and GDPR are followed). These could include applications, email servers, cloud storage, cloud infrastructure and containers. This can be challenging given how prolific cloud usage is across most organisations, however it is crucial that all areas have been considered across all of your users and departments.
Understanding what types of information your organisation processes, stores and transmits is key in the assessment process, and you should consider rating the information in terms of its sensitivity and importance as any sensitive data will need more robust protection from cyber threats. This includes high risk data such as cardholder information, customer or employee records, financial documents, or any type of personally identifiable information (PII) that could be used for extortion, impersonation or financial gain.
You should also identify all of the users in your organisation (and third parties such as contractors and outsourced suppliers) who will have access to the information to understand which of them carry increased risks as part of their roles. For example, staff in IT will have power user permissions which would be attractive for a threat actor to use to gain access to IT systems. Staff in a Finance department will have access to sensitive information which could be exploited by a threat actor for financial gain. Similarly, business leaders, executives and board members also have a higher risk from a cyber security point of view, as they are usually the target of Business Email Compromise (BEC) attacks.
Once that’s done, the next step is to start assessing and calculating risk levels.
The CVSS standard (Common Vulnerability Scoring System) is a well-known framework that is often used by organisations to help identify and manage security vulnerabilities. At the time of writing in August 2023, there were over 16,400 publicly disclosed CVEs (Common Vulnerabilities and Exposures), with an average CVSS score of 7.6 out of 10. This score helps organisations to better understand the impact of the vulnerabilities if they were exploited.
Many organisations have a good understanding on the types of risks that are relevant to their environment, but not what their sources of threat are. If a new vulnerability has been identified, it’s essential to think about who the threat actor would be, or who could exploit a vulnerability in your environment.
In fact, only a very small proportion of vulnerabilities (around 5%) are ever actually exploited. So, if you’ve been alerted to a vulnerability that has a very high CVSS score, but there’s a very low chance of it being exploited (due to mitigating factors or controls that your organisation has put in place), then the risk could potentially be downgraded and not treated as critical as it was first reported.
That’s why the concept of EPSS (Exploit Prediction Scoring System) was created. The difference between CVSS and EPSS is that the EPSS model is used to estimate the probability of a CVE being exploited in the wild. CVEs are assigned a decimal value of between 0 and 1 (0% and 100%), with 1 representing the vulnerabilities that are the most likely to be leveraged by attackers.
Framing a vulnerability in the context of the probability of its exploitability, enables organisations to correctly apply the priority the vulnerability requires. A business can then decide on applying mitigating measures, or risk acceptance in order of how likely the vulnerability is to be exploited, rather than simply tackling all of the vulnerabilities immediately.
Combining the two methods is a much more effective way of prioritising cyber risks and helps to define an overall threat level to the organisation. This would feed into your risk scoring and determine what risk decisions are required.
With the CVSS and EPSS models in mind, the simplest way of calculating cyber risk is by assessing the probability of a vulnerability being exploited, and the expected impact if it did happen.
Many standards such as ISO 27001 do not mandate a particular way to calculate risk, however organisations can do this by using a simple risk matrix.
A risk matrix is a method of visually scoring the impact and probability of a particular risk occurring. This enables you to calculate a risk score that can be used to determine if the risk falls within your risk acceptance level or if the risk requires mitigating measures applied.
One commonly used matric used in risk assessments is the 5x5 risk matrix, as detailed below.
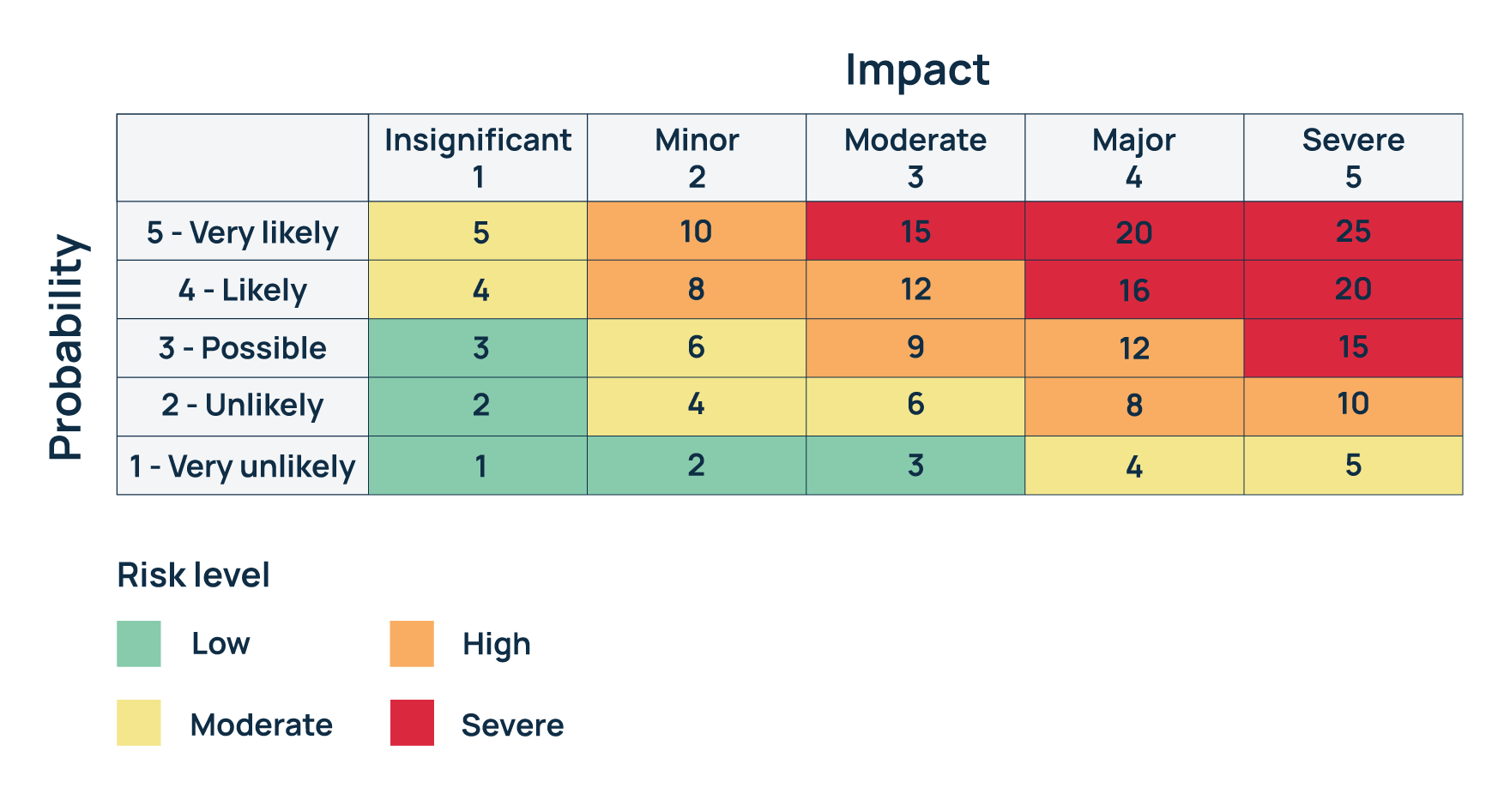
In this example, you can see that both the Probability axis and Impact axis are assigned values from 1 through to 5, with 5 being the most likely and severe respectively.
This is where the CVSS and EPSS scores can come into play and help you use the matrix more effectively. For example, a CVSS score of 5.4 could be mapped to an impact score of 3 (Moderate), and an EPSS score of 0.1 would be equivalent to a probability value of 1 (Very unlikely).
To calculate your risk value, you simply multiply the Probability number by the Impact number. We’ve filled in all of the values and assigned a colour to each one, so that it is easy to identify the general risk level at a glance.
As part of your cyber security risk assessment, you should define what the different risk values mean for your organisation in terms of risk acceptance and tolerance. Here’s an example of how they could be defined:
Based on this scale, your organisation can define a clear path forward for each risk, depending on the value that has been calculated. For example, you could decide that any risk with a score of 10 or more must be actioned, while anything less than 10 can be accepted.
Once you’ve identified, assessed and evaluated your risks, it’s time to document the output so that you can prioritise what risks to focus on first.
Here’s a very simple example of how you can achieve this with the risk assessment results we’ve already covered. Note that each risk has also been assigned an owner:
| Asset | Threat | Vulnerability | Risk Owner | Risk score |
|---|---|---|---|---|
| Windows 10 | Data breach, ransomware | Remote Code Execution (RCE) Vulnerability CVE-2023-21803 |
IT Manager | 20 |
| CRM system | Unauthorised access | Shared passwords | Department Head | 12 |
With your risks clearly outlined, you can document everything that needs addressing in a risk register, and use this as your prioritisation guide. It’s very important to note that a risk register is not static fire and forget document. Instead, your risk register should be used as a risk treatment plan documenting your risks and your management of those risks (treat, tolerate, accept, transfer) until they can be closed.
Your risk register should act as the one version of truth on all cyber risk, documenting the risk owner, the risks mitigations, the risk decisions which are made and to be used to track the ‘cradle to grave’ risk process. This means you will have evidence in place in case you ever need to refer to a particular risk in the future, or provide evidence to an auditor if required.
As we’ve seen, context is so important in all aspects of cyber risk management. While there are many different ways to conduct a cyber risk assessment, the best approach you can take is to tailor your chosen method so that it reflects the unique needs of your organisation. This helps to ensure that the assessment is effective and produces actionable results to mitigate risks.
Regular risk assessments will help you to identify the biggest threats to your organisation and enable you to prioritise the most pressing risks first. Adopting a repeatable and consistent approach to cyber risks, using the steps outlined in this article, will make it easier to understand and defend your organisation against cyber threats and demonstrate good risk management.

Mikey Anderson
Product Marketing Manager
Share this article
Get your free trial of Defense.com and discover how we can help you take the stress out of your cyber security.

A complete guide to getting started with compliance including which cybersecurity and data protection standards…

How well prepared is your business to withstand and recover from a cyberattack? Discover best practice advice…

ISO 27001 is an international standard for information security management (ISMS). Discover everything…

Learn about the security risks involved with cloud computing, how to secure your data, and risk management best practices.…
Get actionable cyber security advice and insights straight to your inbox.