
Fighting fatigue: 5 ways to avoid cyber burnout
Ignoring the warning signs of cyber burnout can have serious consequences both for you personally and…



Mikey Anderson
Product Marketing Manager
5th February 2024
Millions of organisations around the world rely on Microsoft 365, so it’s no surprise that it can be a prime target for attackers. While organisations are leveraging the power of Microsoft 365 to enhance productivity and collaboration, they are also exposing themselves to an ever-evolving threat landscape.
Although SaaS solutions like Microsoft 365 can provide organisations with various ways to detect and protect against cyber threats, this doesn’t mean that it makes your environment immune from attack. From phishing attacks and data leaks to business email compromise (BEC) and insider threats, there are many different risks that could affect your organisation that involve Microsoft 365.
So, what can be done? As well as taking preventative measures to defend against cyber threats, continually monitoring for signs of malicious activity is equally as important. The evolving nature of cyber threats demands more proactive measures to identify them and take action before they are exploited.
Microsoft does provide a variety of dashboards to help organisations monitor threats, however with so many different places to monitor, alert fatigue and burnout can quickly set in, making it difficult to know where to focus first. Remediation guidance is also limited, which means it can take more time and effort to investigate and respond to threats.
To combat these challenges, Defense.com has launched an integration for Microsoft 365 to help make your cyber security easier to manage. This API integration aims to address the evolving threat landscape for Microsoft 365, helping you to detect and respond to cyber threats faster and more efficiently.
By using the Defense.com integration for Microsoft 365, you can get alerted to new threats, improve your Secure Score and receive tailored security recommendations. This will enable your organisation to:
Get instant security alerts for your Microsoft 365 account and users to detect malicious activity.
Make threat management easier by combining telemetry from your whole security stack in one place.
Strengthen your security with clear remediation advice and actions to improve your Microsoft Secure Score.
Let’s dive into the main features that we have introduced with our Microsoft 365 integration and how they can help your organisation manage security threats.
The Defense.com integration for Microsoft 365 is completely agentless and gathers telemetry using the Microsoft Graph API. This collects a variety of logs and security alerts from Microsoft 365, including your organisation’s Microsoft Secure Score and events from Microsoft Entra ID.
The integration process is straightforward and takes a matter of minutes, with a simple, step-by-step wizard that guides you through each stage. With just a few clicks, you’ll be connected and sending security telemetry directly to your Defense.com account.
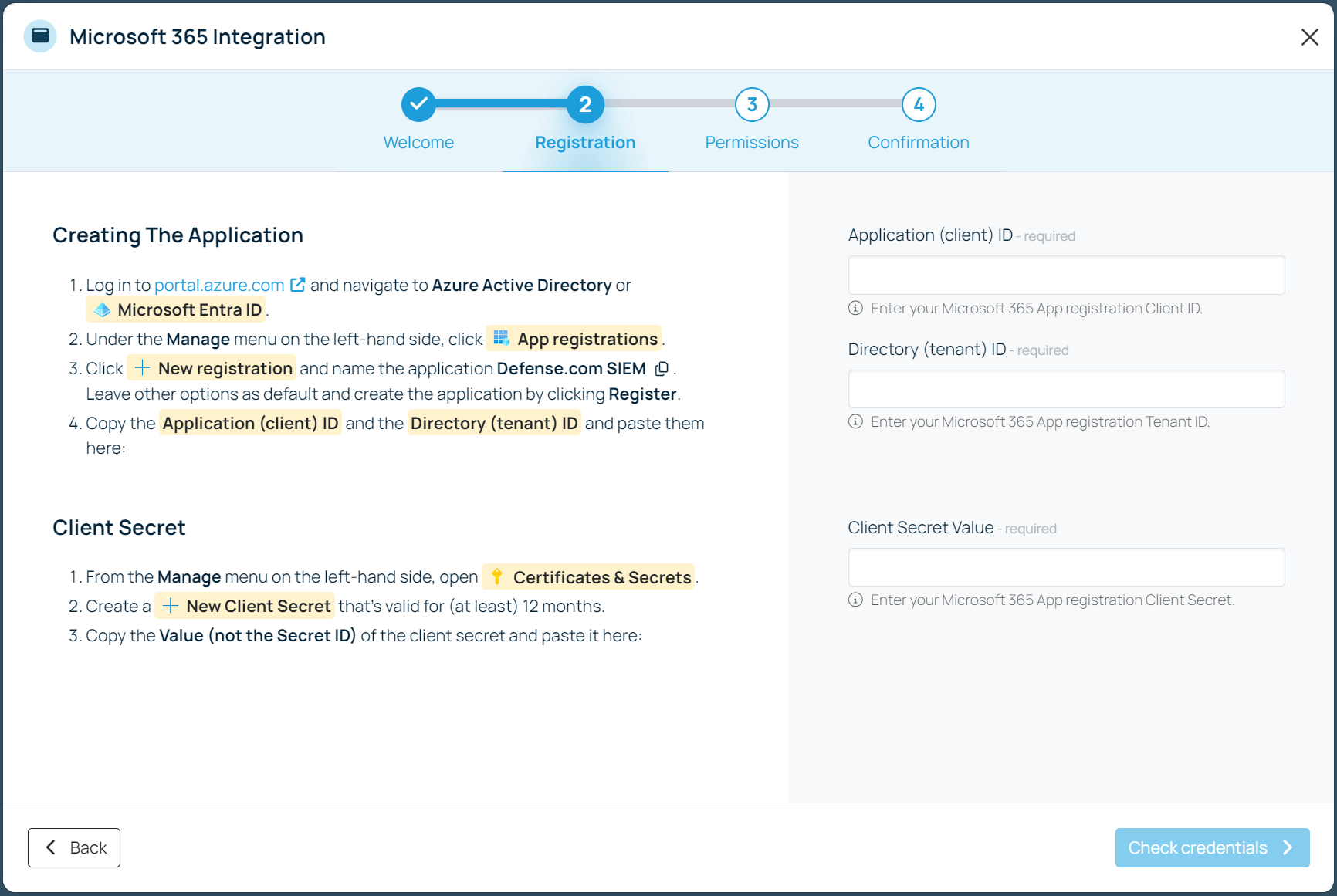
Microsoft 365 and Microsoft Entra ID (Azure AD) can generate a wide range of alerts that serve as potential indicators of attack (IoAs) and indicators of compromise (IoCs). In Microsoft Entra ID Protection, these alerts are referred to as 'risk detections,' and they can originate from either the user or sign-in level.
As part of this integration, Defense.com will alert you to a variety of security alerts affecting your Microsoft 365 account and users. Examples of alerts raised include:
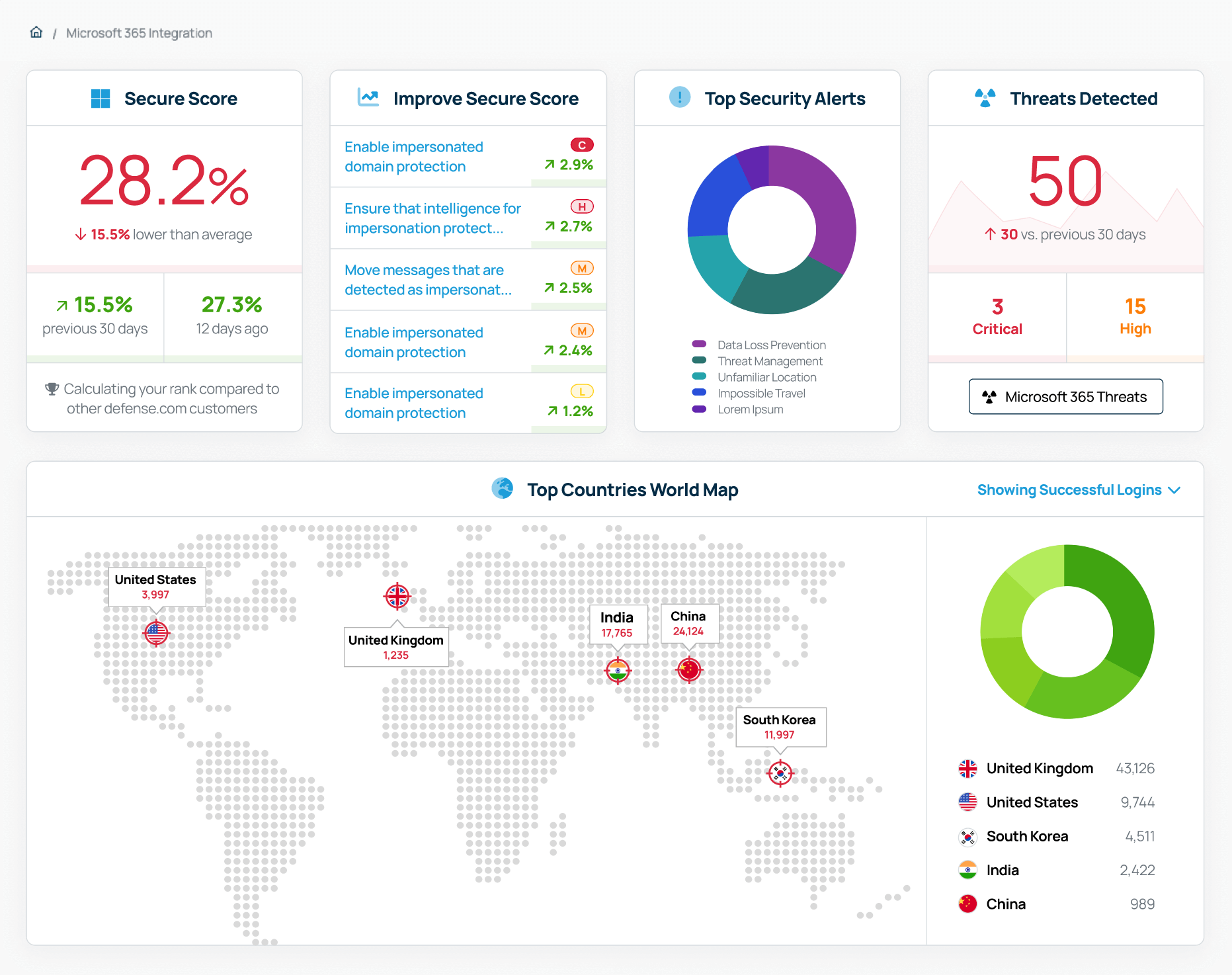
By monitoring these types of alerts in Defense.com, you can quickly detect suspicious activity across your Microsoft 365 environment. Each alert will contain detailed information about why and how it was triggered, giving you further context to aid investigations and threat response.
Gain expert insights from the Defense.com SOC team on how to improve your detection and response to Microsoft 365 security alerts.
Managing Microsoft 365 threats can be challenging when alerts are raised in different places throughout the Microsoft ecosystem, especially if you have a small team with limited resources.
Defense.com makes this task easier to manage by bringing security telemetry from Microsoft 365, and all other areas of your environment, into a single platform. Instead of switching between multiple Microsoft dashboards and menus, with Defense.com you can simplify your security operations by combining all your threats in one place
Each threat is prioritised in order of criticality and contains step-by-step remediation guidance, so you know exactly what to focus on first and how to fix it. This helps you speed up detection and response times, so you can find and fix issues before they are exploited.
As part of this integration, a bi-directional sync with Microsoft is also configured. This means if you remediate a threat in Defense.com, this will show as remediated in your Microsoft 365 account and vice versa. This helps you to focus on managing threats in your Defense.com account without having to duplicate effort in Microsoft 365.
For clients on our Managed SIEM service, once these alerts have been investigated and contextualised by our SOC team, you will get tailored security events based on your business profile. This helps to keep false positives at a minimum and ensures that you are only getting genuine threats raised to your attention. You can still view specific alerts yourself at any time via your Threat List, or search for particular logs in a given time period.
Your organisation’s Microsoft Secure Score is a good overall measure of its security posture. Defense.com simplifies the process of enhancing your Secure Score by providing clear, actionable steps and demonstrating the impact of each action on your score.
Each recommended action will be tailored to your organisation, covering a variety of areas to help you improve your Microsoft 365 security. You can also see how your Secure Score compares to other organisations and track your score over time.
Setting up the Defense.com integration for Microsoft 365 only takes a few clicks. Simply log in to your Defense.com account today to get started, and the integration wizard will guide you through the process.
You can also check out the following additional resources:
Defense.com is an XDR platform that helps IT and SecOps teams easily identify, prioritise and remediate cyber threats. Businesses of all sizes rely on Defense.com to detect and respond to threats, stop cyberattacks and strengthen their cyber security posture.

Ignoring the warning signs of cyber burnout can have serious consequences both for you personally and…

How well prepared is your business to withstand and recover from a cyber attack? Discover best practice…

Read our introductory guide for everything you need to know about log monitoring. What it is, how it works…

Find out how ransomware works and read top tips for defending against attacks by securing your business…
Get actionable cyber security advice and insights straight to your inbox.