
Oliver Pinson-Roxburgh
CEO and Co-Founder
17th June 2022
Many businesses are facing similar challenges with their threat management, including a lack of visibility, skills, and the tools to identify, investigate and respond to threats quickly and effectively. Threats are becoming common and sophisticated, and this is leading to organizations facing the threat of a cyberattack and data breach more frequently. In 2021, the global cost of data breaches rose to $4.24 million.
To help our customers manage cyber threats with greater proficiency, we’ve developed our threat management tool by adding new features to enhance its existing functionality. This blog will explain how our new features will help your business manage your threat landscape more efficiently, how they address common threat management challenges, and why they can be beneficial in increasing your threat detection and remediation output whilst staying on top of your most critical risks.
What is threat management?
When we talk about threat management, we refer to the framework that cybersecurity professionals use to manage the lifecycle of a cyber threat. Minimizing a cyber threat requires rapid detection and response to safeguard your business and its data. However, effective threat management goes beyond identifying and responding to cyber threats. Without visibility and control over your network environment, you’ll have very little chance of defending against data breaches. You can’t defend what you can’t see, so it’s important to ensure you have the tools in place to proactively monitor, detect and address those threats to your business.
Threat management is crucial for businesses, now more than ever, because it improves collaboration across people, processes, and technology, providing you with the best chance to spot risks early and respond rapidly.
Threat management can also help your business keep track of the threats you are facing and streamline the overall process. That is why our threat management tool was built with simplicity and usability in mind, to help businesses identify, prioritize and remediate threats with minimal effort.
What’s new?
With innovation and simplicity in mind, we’ve made significant improvements to the threat management capabilities in Defense.com™, which includes new Threat Dashboard and Threat List features to enhance your user experience. Here’s a rundown of the key changes:
Threat Dashboard updates
-
Enhanced visibility
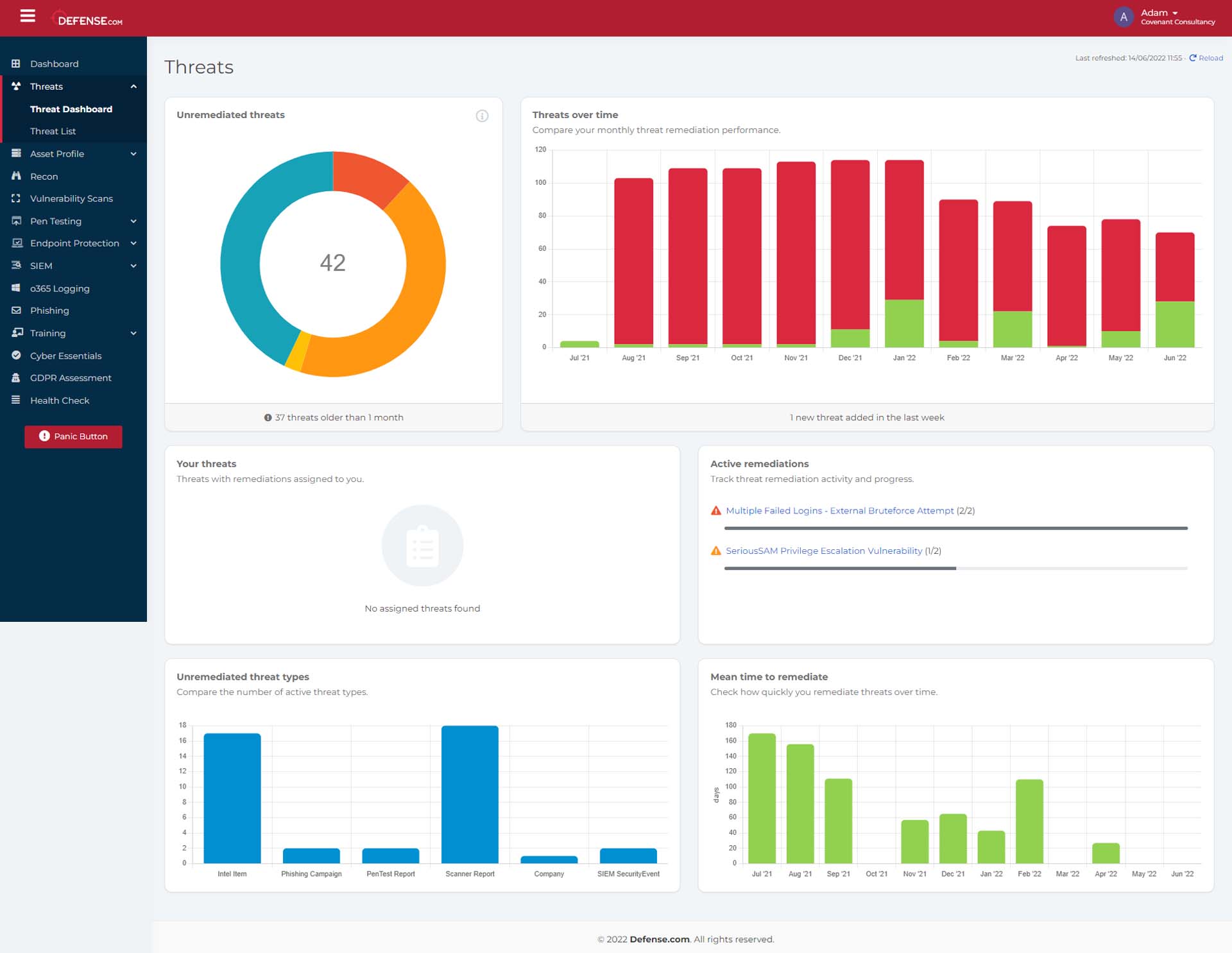
One of the biggest challenges we heard from our customers was that traditional threat management tools do not provide visibility of their entire threat landscape. IBM estimates that enterprises use as many as 80 different security products from 40 vendors. That’s an alarming number of solutions to manage and threats to track, especially for organizations with limited resources. In Defense.com™, your Threat Dashboard solves this issue by merging all of your threats, from penetration testing, vulnerability scanning to endpoint protection, into a single user-friendly dashboard.
Your Threat Dashboard also allows you to see your threat remediation performance over a 12-month period. With greater visibility over your risk counts, you can assess how well you’re performing and compare and assess your remediated and unremediated threats. This is an important feature as it gives your business unified insight into whether your security team (or third-party service provider) have taken action on the most critical threats that pose a risk to your business.
-
Assign threats to multiple users
We wanted to address the challenges many IT teams have when monitoring and responding to threats – productivity and fatigue. Security teams can receive more than 500 security alerts per day and that can quickly lead to burnout. That’s why we’ve introduced a new feature that allows you to assign active threats to multiple users and help distribute remediation efforts across your team.
We’ve built this feature to streamline the management of threats, improve efficiency and productivity by viewing all of the threats currently assigned to a specific user. This will help alleviate the pressure on IT teams that are having to deal with multiple threats at any given time. Additionally, by giving the ownership of threats to specific individuals in your organizations, or third-party vendors, it is easier to track and manage your threats.
-
Active remediations
Track the progress of any ongoing remediations and follow any associated activity in real-time. This makes it simple to return to each phase of the remediation process and continue resolving threats.
Unremediated threat types
You can now view your unremediated risks in your Threat Dashboard to gain a better insight into your existing threats. This will help you easily identify the source of your threats and the number of threats emanating from that source. For example, if a threat comes from a phishing campaign or unpatched application, this will indicate the need to deploy additional security training to employees and update that specific application.
-
Mean time to remediate
Proactive detection and response are key elements to threat management. From your Threat Dashboard, you can track the average time it takes for you to remediate a threat. The quicker you can remediate threats across your organization, the quicker you can protect your environment and prevent any vulnerabilities from being exploited. This feature can also help your business keep track of the performance of your team and third-party vendors against KPIs, to ensure expectations of threat remediation are being met.
-
Automation
As cybercriminals use automation to sophisticate and speed up their attacks, a threat management tool should leverage automation to improve the speed and efficiency of your threat response and effectively manage your security risk. Within your Threat Dashboard, threats are automatically assigned a level of criticality that determines the likelihood of a vulnerability being exploited and the potential impact of the threat. This feature will enable you to prioritize your threats and ensure you are aware of the most pertinent risks currently posing a risk to your organization.
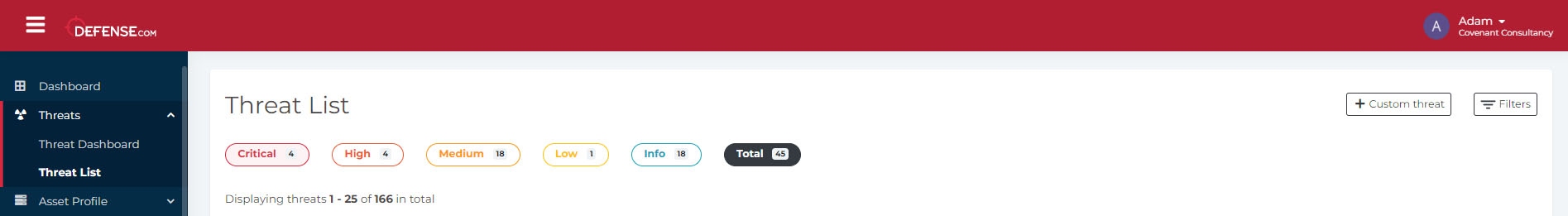
Threat List expansion
We’ve also expanded the functionality of your Threat List in Defense.com™. By improving its functionality, you will receive a clearer overview of the criticality of each threat. So, what’s new?
-
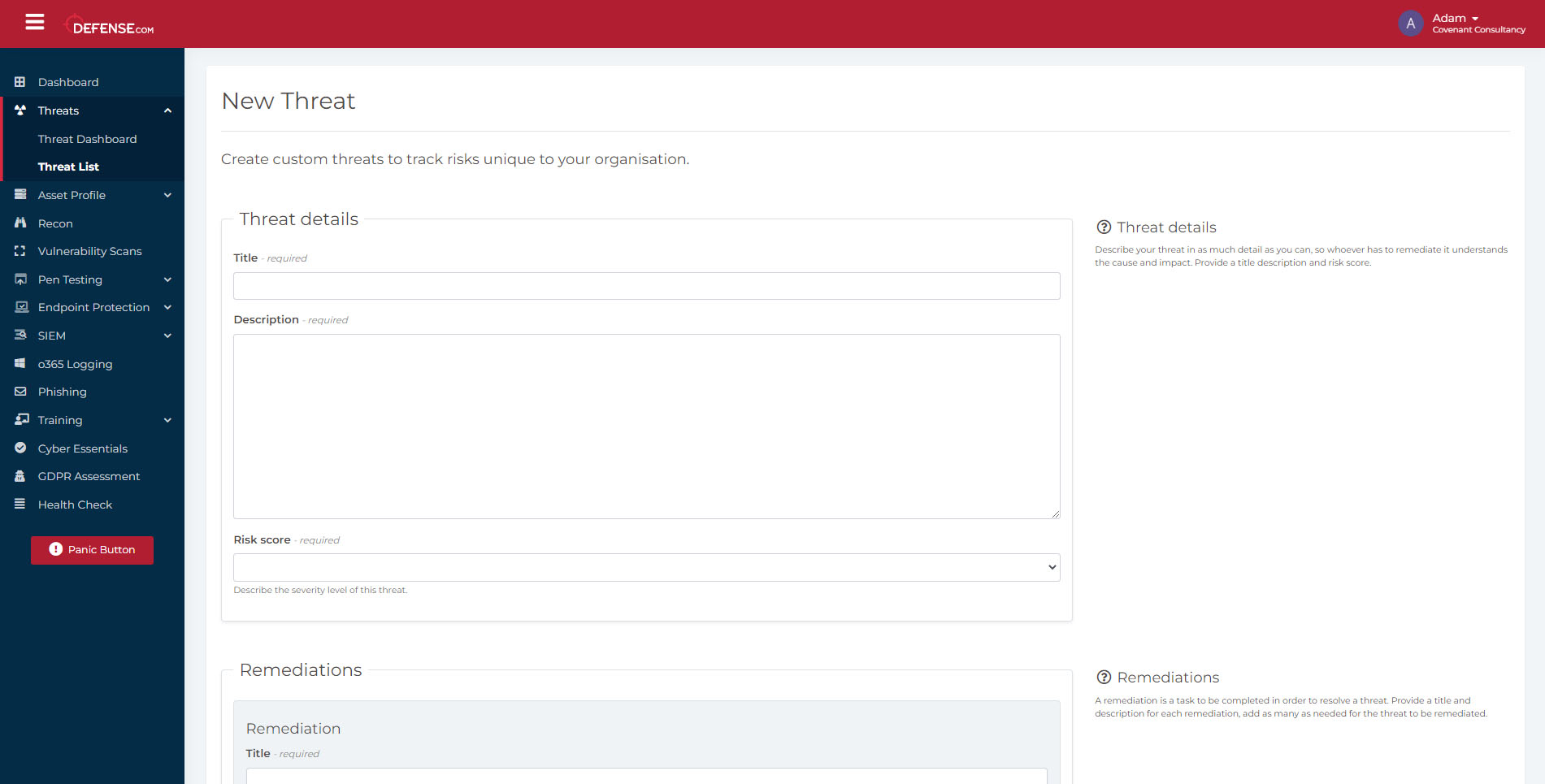
Add custom threats
Manage your risk landscape and test your security by adding custom threats that are unique to your organization. Changes in your infrastructure, whether it’s updating your operating system, migrating to new cloud platforms or installing new software and devices, can all introduce new threats. If there’s a specific threat that you’re concerned about that isn’t covered by any of the features in Defense.com™, you can simply add a custom threat to your Threat List. You can select a risk score to highlight its urgency and include remediation instructions to ensure all aspects of the threat have been mitigated.
-
Accepting risks and false positives
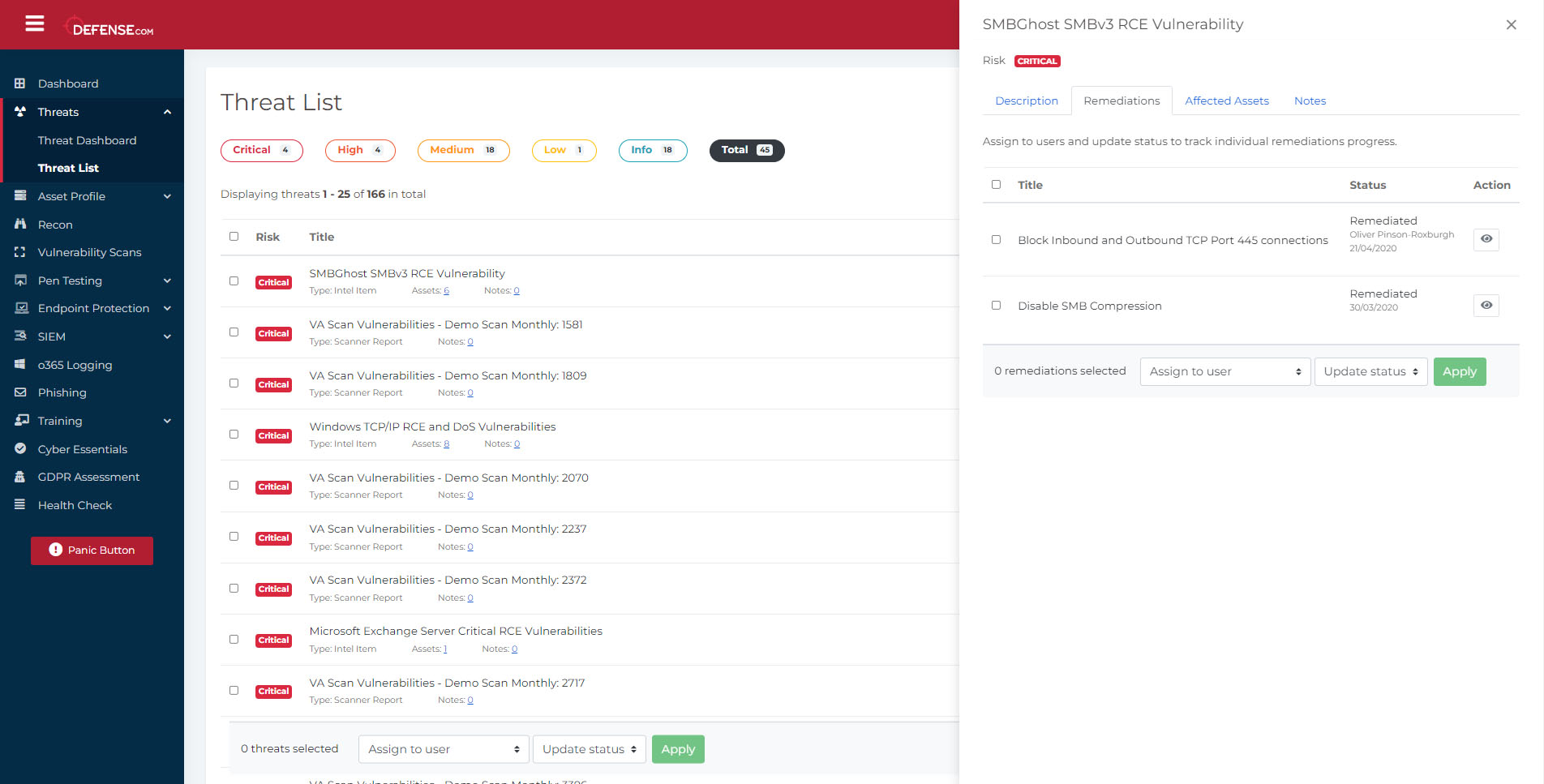
As part of the remediation process, you now have greater control over accepting specific risks and threats that can be marked as false positives or accepting a certain level of risk. If you have multiple security systems in place, from firewalls and endpoint protection to SIEM, these can all flag up false positives that indicate a vulnerability or threat where one doesn’t exist. In Defense.com™, you can now mark such threats as false positives and allow you to accept the risk of a threat to ensure it has been noted and that it is recorded in an audit trail.
Similarly, you can now also mark threats as ‘risk accepted’ if you need to carry on without remediating them, either because a remediation is not currently possible, or because your organsiation is willing to accept that level of risk. This should be selected with caution, though, as remediation should be the first choice of action wherever possible.
-
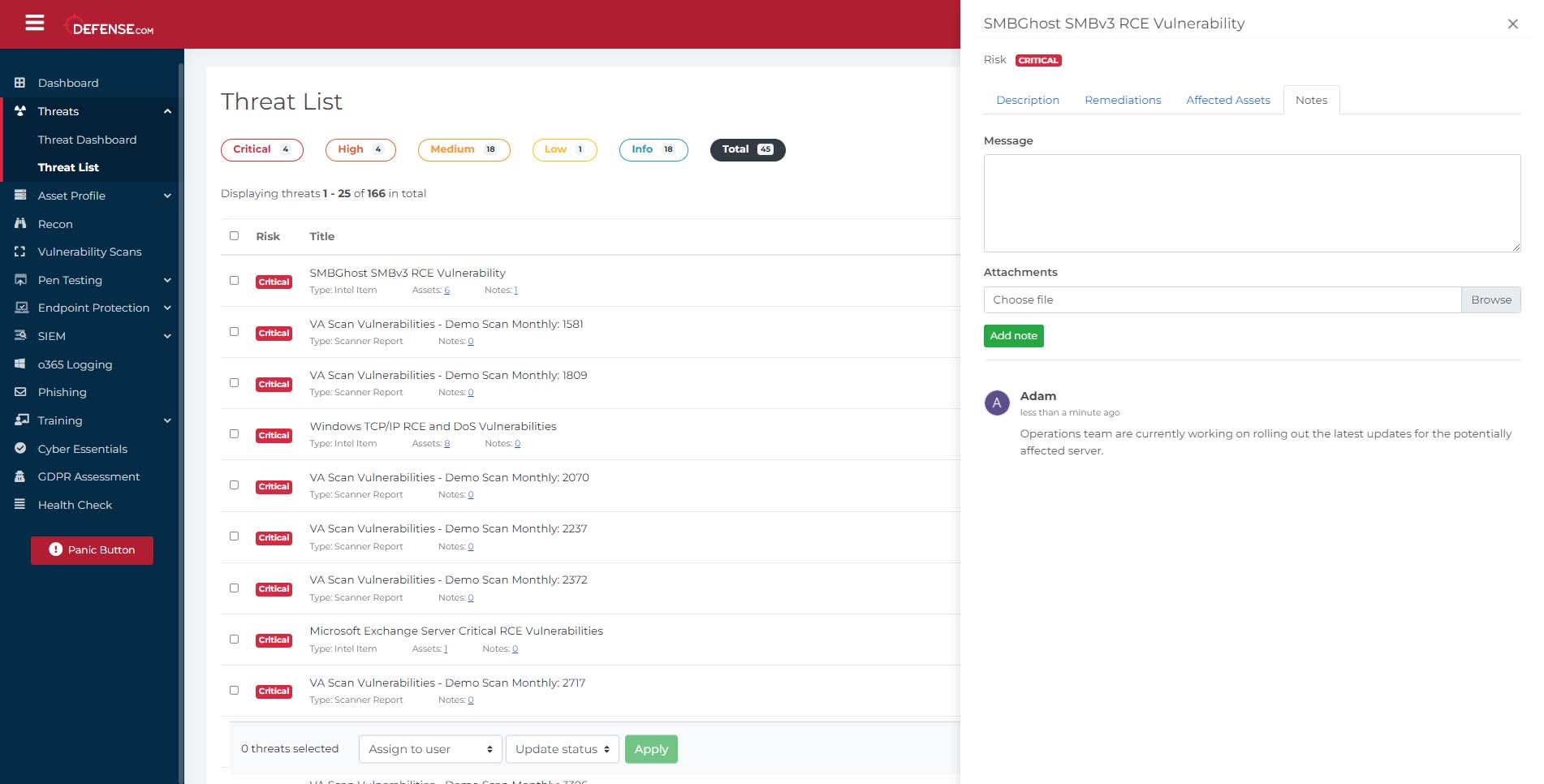
Add notes
Users can add notes to a threat and also log updates to aid with investigation and remediation, encourage collaboration, and develop an audit trail of actions taken against a threat. Notes allow your team to reassign threats with greater detail and peace of mind if employees are absent due to sickness or holiday leave or require additional support to remediate a specific threat (for example, from a third partner support provider).
-
Bulk updates of threat status
We had several requests from our customers to be able to carry out bulk actions in their Threat List to increase their efficiency and remediate threats faster. We’re happy to announce that this is now live in your Defense.com™ account! You can now bulk update the status of threats and bulk assign remediations to specific users. Bulk updates will also allow you to maintain a more comprehensive and up-to-date audit trail of ongoing remediation activity and previously completed threats.
Summary
The threat management capabilities of Defense.com™ can be used as a proactive prevention mechanism that ensures your organization stays on top of the threats you face on a daily basis. Early threat detection will maximise your chances of investigating and remediating threats before they are exploited, and the more proactive you are in doing so, the greater the chances of protecting your business.

Oliver Pinson-Roxburgh
CEO and Co-Founder
Share this article


