
The importance of involving channel partners in IT security
Through years of helping businesses improve their IT security, we’ve heard many times that small businesses feel particularly underserved…




Brian Wagner
Chief Technology Officer
25th September 2021
As an IT manager, you’ll know that cybersecurity is a specialist subject with its own skillsets, certifications, and technologies. Unfortunately, you’ll probably also know that commercial realities mean the job of protecting a business against cyberattacks often falls to the IT team. So we’ve assembled 10 things IT managers should know to help them manage their organization’s cybersecurity and, ultimately, keep their business secure.
Cyberattacks are an inevitable part of business operations. In 2020, according to the NCSC, four in ten UK businesses (and over a quarter of charities) reported being attacked or having a data breach. The real numbers are likely to be much higher, as many businesses lack the capability to detect an attack. Certainly almost every IT manager would report weekly, if not daily, attacks from phishing emails trying to bypass spam filters.
The impacts of ignoring cybersecurity are potentially severe, and can include:
To compound the problem, these can all lead to other effects, including:
Despite this, some IT managers put security on the back-burner and treat it is an optional extra. With research showing that up to 66% of businesses go under after a significant cyberattack, ignoring cybersecurity obligations is clearly unwise. For those IT managers who do recognize the importance of cyber but struggle to get in on the board agenda, a good tip is to make the impacts and outcomes as simple as possible for the board.
Defense.com’s threat intelligence gives an overview of active threats and remediations in-progress. This kind of top-level breakdown is exactly what the board want to see, rather be blinded by technological detail, and it also helps show that security spending is an investment, not a cost.
The cyber kill chain codifies each stage an attacker goes through in any given cyberattack. There are several stages and attackers may fail (or be foiled) at any one of them. Increasingly, IT managers are mapping their security investment to each stage of the kill chain to generate a more a effective cyber defense strategy, as it gives the power to detect and stop attacks no matter what stage they’re at.
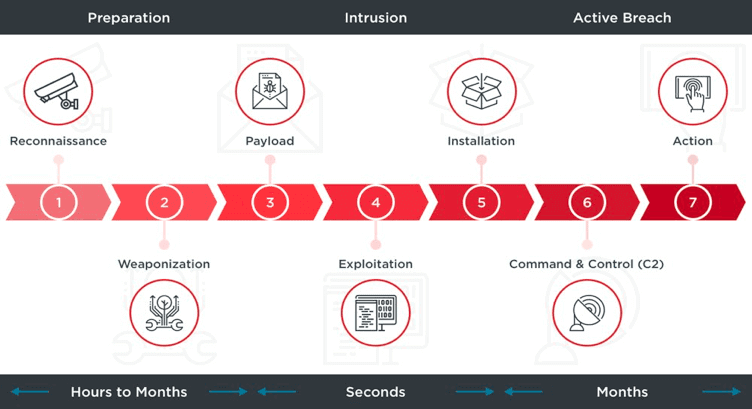
The challenge comes in implementing this in the real world – multiple vendors and disparate technologies make security management a resource-intensive task. This means less clarity of your security oversight and ultimately, more room for hackers. Defense.com™ changes this by giving a business everything it needs in one place. For example, a Defense.com™ recon scan shows you what a hacker sees when profiling your organization, helping you secure the first stage of the kill chain. Likewise later stages are covered too, with Defense.com’s log monitoring delivering the ability to detect and stop attacks in-progress before your security perimeter is breached.
Whilst hackers are known to directly target businesses of all sizes, from multinationals right down to start-ups, many IT managers still think that because of their business’ size or sector, they’re unlikely to be targeted. The biggest flaw in this logic is the fact that you don’t have to be targeted to be attacked: you can just be collateral damage. Hackers regularly send out high volumes of low-tech attacks and, if you’ve not covered the basics, your business will get caught in the crossfire. This is exactly what happened to the UK’s NHS in 2017 when it was hit by the now-infamous WannaCry ransomware. The NHS wasn’t directly targeted, yet it still found itself crippled because of a simple missing Windows security patch. Next time it could just as easily be your business. Even if there’s nothing of immediate value on a compromised system, it’ll likely be roped into a hacker’s botnet, and many hackers will relish the opportunity to test their skills and see if they can pivot to more valuable systems.
This means that having oversight of your security vulnerabilities should be a top priority for every IT manager with cyber responsibilities, and the best way to achieve this is with a penetration test. Defense.com’s penetration tests are easy to schedule, and their comprehensive report gives both a top-line executive summary and a crucial technical breakdown. Plus vulnerability scans are included as part of every Defense.com™ package, helping you keep on top of new threats in between penetration tests.
No matter how big an IT manager’s budget, it seems there’s always more that needs to be procured. Within the strict realm of cybersecurity, however, the trick is to spend wisely, not freely. This means covering the basics first, then strategic value-adds as highlighted by your specific risk profile. This is sometimes called the ‘unicorn strategy’, as it delivers very high value and a strong security posture. The basics for most companies are universal: run penetration tests once a year, run VA scans monthly, make sure your staff know the cyber basics, and get Cyber Essentials certified. These 4 simple steps will mean your organization effortlessly defeats the overwhelming majority of opportunistic attacks, and even some more targeted ones.
Defense.com™ provides all these elemental cybersecurity services and more, starting from just £66 per month. Plus its powerful threat dashboards help you prioritize the cyber risks facing your business, enabling you to spend wisely on defenses that are directly relevant.
The slew of acronyms that make up most compliance standards often strike fear into the heart of an IT manager, most notably GDPR and ISO 27001. Managing the IT elements of compliance standards is often seen as a blocker of business agility and a cost overhead. But the truth is that if done correctly, compliance can help, not hinder.
True compliance means embedding the principles as processes, and embedding the processes as part of your business culture. And that cultural integration can only be achieved with low-friction implementation of the various IT controls that such security standards require. Defense.com™ meets many of the technical requirements of many compliance standards, including:
It does this through its cyber defense capabilities, including:
Smooth integration of these controls means a better experience for IT managers and end-users alike.
Get outsourced help with compliance. There are expert providers who’ve already solved the problems your facing for other organizations. Using their expertise and knowledge will be quicker and cheaper than having to discover and solve the problems yourself.
With Defense.com Assessors, Cyber Essentials certification & CE+ Certification as never been easier!
Learn more about Cyber Essentials
It’s human nature to trust people and brands we’ve heard of, and for IT managers, that’s lead to attitudes such as “no-one ever got fired for buying IBM”. However the reality is that’s not been true for some time, and when it comes to security, that attitude could actually threaten your security integrity. Finding a security partner with a stand-out reputation will reap more rewards than choosing one based on market share alone, where even larger organizations might find themselves as ‘just another customer’. A security provider who shows innovation and demonstrates their understanding of SMBs and enterprises’ various challenges is likely to provide a much more value-packed service. For example, a pen test provider who has broad experience in other areas of security will give a better service thanks to having more niche skills and a better understanding of your challenges, all of which come from team collaboration and customer insights. This dynamic approach simply isn’t possible with the siloed approach of monolithic security providers.
The different service tiers of Defense.com™ enable businesses of all sizes to get a best-fit security service that meets the needs of your business. Plus its services are backed by a state-of-the-art SOC, giving extra intelligence and depth of knowledge to Defense.com’s services.
Every IT manager knows that patching gets harder as an organization grows, but it doesn’t get any less important. In fact, thanks to the challenges presented by shadow IT and BOYD, having an up-to-date patching regime becomes more important as a business grows. The 2021 Bulletproof Annual cybersecurity Industry Report showed that 32% of all critical security vulnerabilities detected in penetration testing were just missing patches. For IT managers dealing with legacy or delicate production equipment, you may need to treat the risk by a method other than patching, but both the risk and its remediation still needs to be identified and tracked.
Defense.com™ makes it easy to identify, track, prioritize and remediate all security threats, regardless of severity or origin. This ‘single pane of glass’ approach greatly simplifies the management of an organization’s security, and can also help keeping on top of ISO 27001 requirements. In particular, Defense.com’s Asset Manager feature makes it easy for you to identify and track of all the operating systems and devices used within your business. This enables the ability to gain a birds-eye view of your cyber risks and remediations across your entire infrastructure.
Does your endpoint join up with the rest of your security services? A mature MDR service that includes endpoint gives good coverage, and a holistic overview of your entire organization’s security will help detect, prioritize and control cyber risks.
The events of 2020 changed the game for business continuity and security. Almost overnight, whole businesses pivoted to a new way of working, which for IT managers meant hasty procurements, rushed implementations and ‘good enough’ operations. For many businesses this meant operating outside the walls of their security investment. Now normality has resumed, the challenge IT managers face is adjusting operations so that the workforce is once again inside that security perimeter. At the same time, employee expectations on remote working have changed, with varying degrees of remote working now the norm. This means your standard security landscape now includes more mobile devices, more locations and more home WiFi routers.
All this highlights the increasing importance of endpoint security in the new normal. To mitigate the new risks, modern endpoint protection, such as that included in Defense.com™, needs to go beyond simple anti-malware. Endpoint security should have the capability to detect, isolate and contain your compromised user devices, and be within the oversight of a managed SIEM service.
It’s a rare that an IT manager won’t be responsible for managing cloud-based services within a business, and whilst the focus will generally be on availability and operational effectiveness, security can’t be overlooked. The received wisdom is that cloud services already have security taken care of. And whilst it’s true that the larger providers might cover the basics, smaller vendors might not even do that. There is another point to consider: how do you know what security risks a cloud service provider presents to your organization? Outsourced service is not outsourced responsibility. Just because it’s not your server or service, doesn’t mean it’s not your data at risk. And that means you need to check. Many cloud infrastructure providers will let you pen test their services without even having to inform them, but security should start, not end, with a penetration test.
In addition, the gray areas caused by the shared responsibility model leaves some businesses unclear on who’s responsible for what when it comes to security, and the myriad configuration options, such as those in AWS and Azure, mean that security holes can be added entirely innocently, and unknowingly. These obviously need to be detected and remediated, and leaning on existing experience can pay dividends here. Defense.com’s security consultants have a wealth of experience in reviewing cloud configurations, and can quickly tell you what risks are present and how to secure them. This kind of outsourced help leads to a quicker, and less costly, resolution.
We’ve saved the best ‘til last. Aside from the rollout of a new program or service, training is not often considered part of an IT manager’s remit. However, security training has the potential to be the best weapon in your security arsenal. Consider this: Even expensive security investments can be undone by your end-users:
But preventing these kind of human-based risks can be easily (and cost-effectively) achieved with security awareness training. Having an employee base that’s aware of their cyber responsibilities, and the security implications of their day-to-day actions, can turn a weakness into a strength.
Though ‘training’ often conjures up images of long and boring PowerPoint presentations, modern training is
Defense.com™ includes security awareness training for all employees, and covers everything an IT manager needs to worry about, including email security, data protection, passwords, malware and more.
The relationship between employee and IT Dept should be positioned as a partnership. If IT (and IT security) can be seen as an enabler of secure business operations rather than a blocker of productivity, the problem of shadow IT fades away and staff become actively engaged with security. This can be further enforced by having data protection compliance (GDPR, ISO 27001) embedded as a culture within an organization.
In this blog we’ve walked through the details of 10 things IT managers need to know about cybersecurity, including how Defense.com™ can help. To recap:
Defense.com’s tools can help simplify the management of cyber risks for IT managers, and help IT managers get board-buy in for cyber investment.
Increase your effectiveness by aligning your cybersecurity strategy to the kill chain. This is made easy with Defense.com’s suite of powerful cyber defence technologies.
Defense.com’s pen testing gives quick, accurate oversight of all your security vulnerabilities so you can avoid both targeted and untargeted attacks.
The powerful threat dashboards in Defense.com™ help you prioritise the cyber risks facing your business, enabling you to spend wisely on defenses that are directly relevant to your risks.
Defense.com’s cyber protection technologies help with the smooth implementation and integration of ISO 27001, GDPR and Cyber Essentials technical controls.
Innovation is at the core of Defense.com™, and the different service tiers enable businesses of all sizes to get a best-fit security service that meets the needs of your business.
Defense.com™ makes it easy to identify, track, prioritise and remediate all security threats, regardless of severity or origin.
Endpoint from Defense.com™ goes beyond simple anti-malware with additional features to help counter the modern threat landscape.
Defense.com™ includes expert security consultancy, which leads to a quicker and less costly resolution for problems such as secure cloud configurations.
Security awareness training is included for all employees through Defense.com™, and covers email security, data protection, passwords, malware and more.

Brian Wagner
Chief Technology Officer
Share this article
Get access to comprehensive security tools and expertise, without the enterprise price tag.
No advanced knowledge required – we'll take care of the heavy lifting for you.
Find out more about the 7 steps to securing your business and sign up for a free trial today.

Through years of helping businesses improve their IT security, we’ve heard many times that small businesses feel particularly underserved…

Cybersecurity training and general security awareness is vital to protect your business…

Cyberwarfare is a present-day threat when conflict between two nations develop, with…
Get actionable cyber security advice and insights straight to your inbox.