
Everything you need to know about phishing
Read more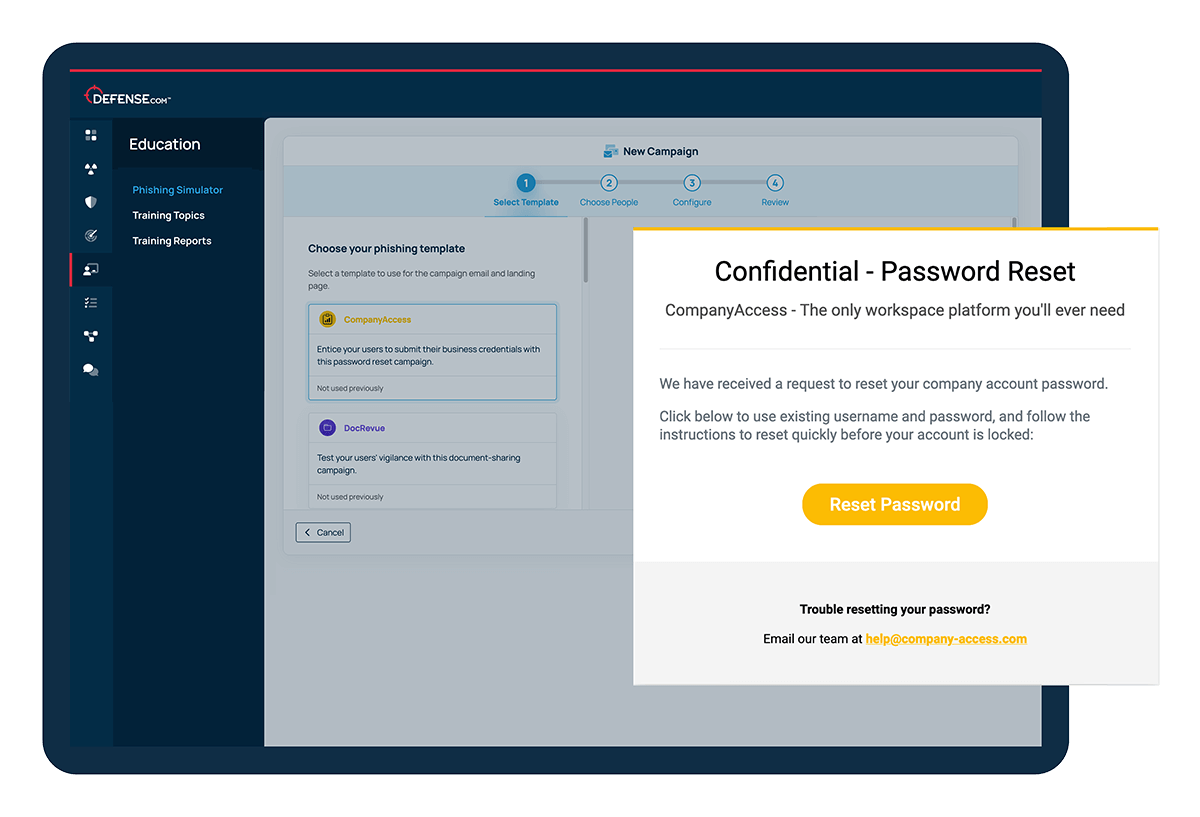
Test if your staff can spot and avoid malicious emails with the Phishing Simulator in Defense.com
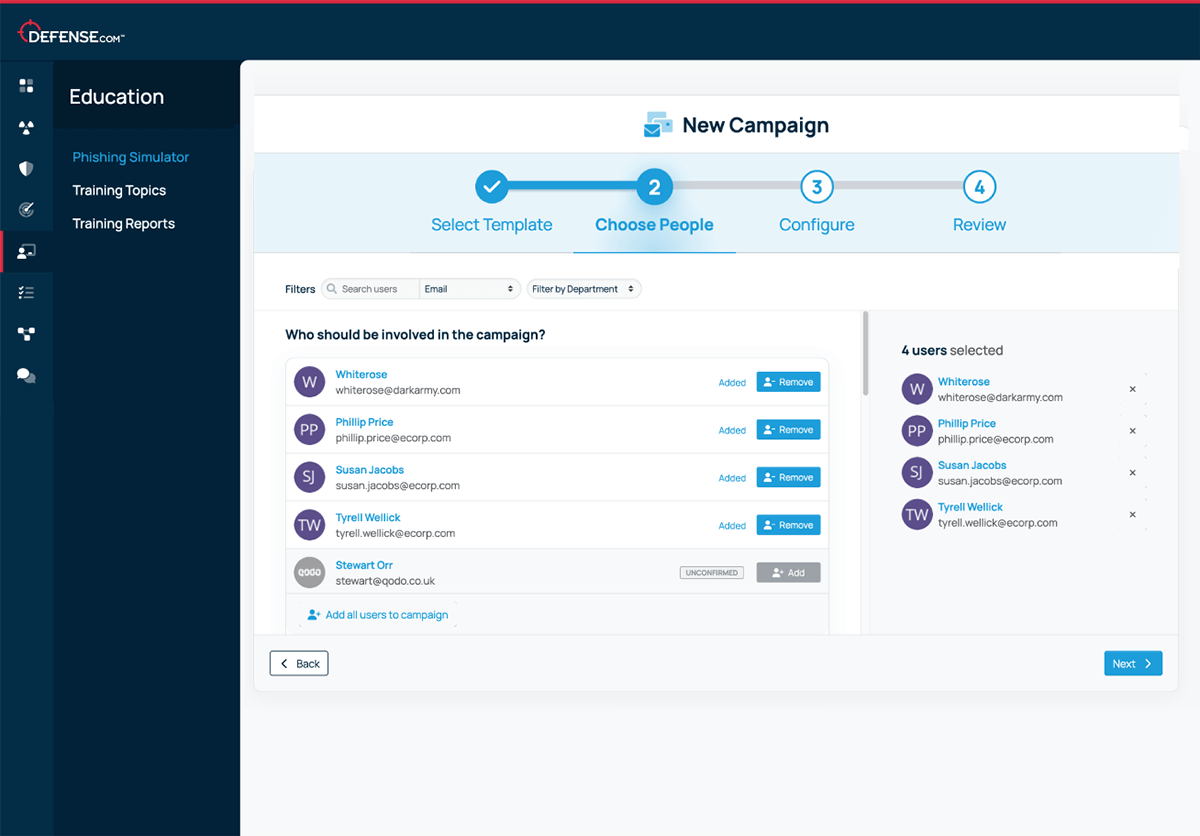
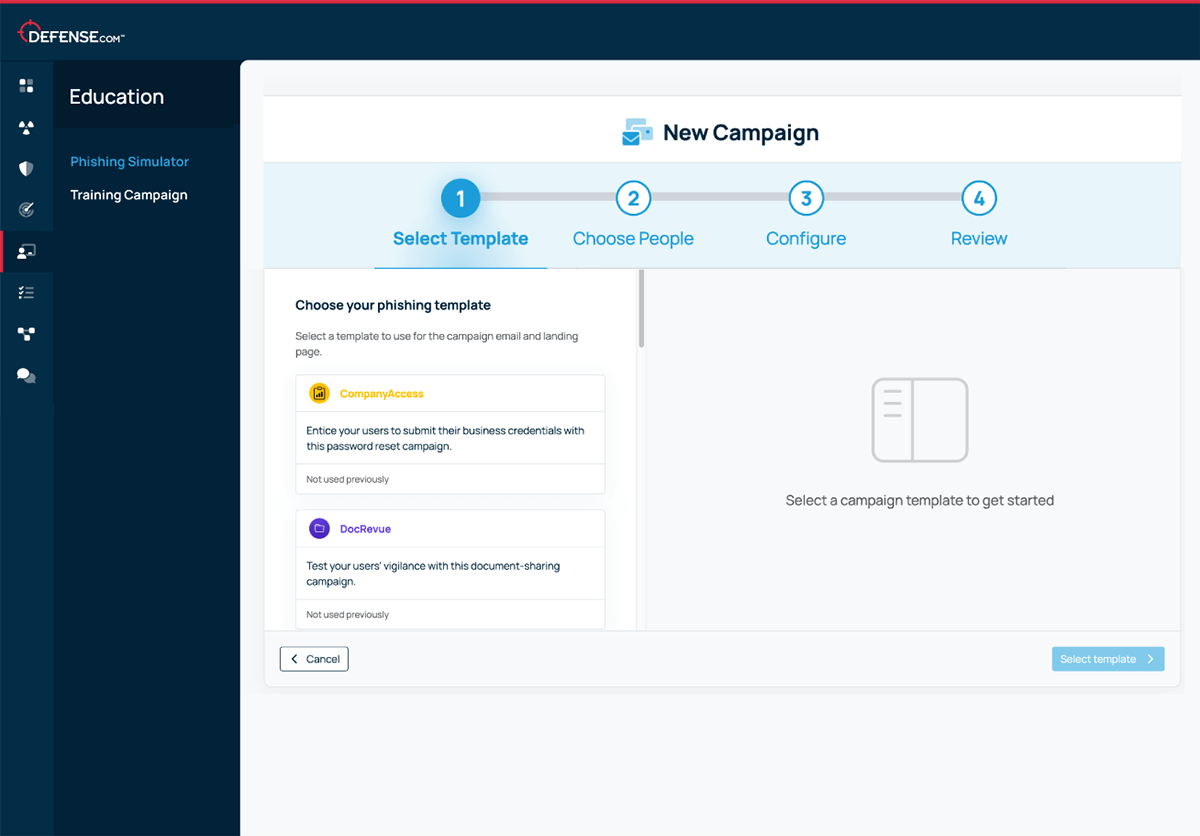
Our streamlined 4-step setup lets you easily launch targeted campaigns by department. Choose from a variety of pre-prepared email templates to identify vulnerabilities and provide tailored training where it’s needed most.
Try for free





























See how easily you can create phishing simulations, track user responses in real-time, and turn learning insights into actionable security awareness training for your team.
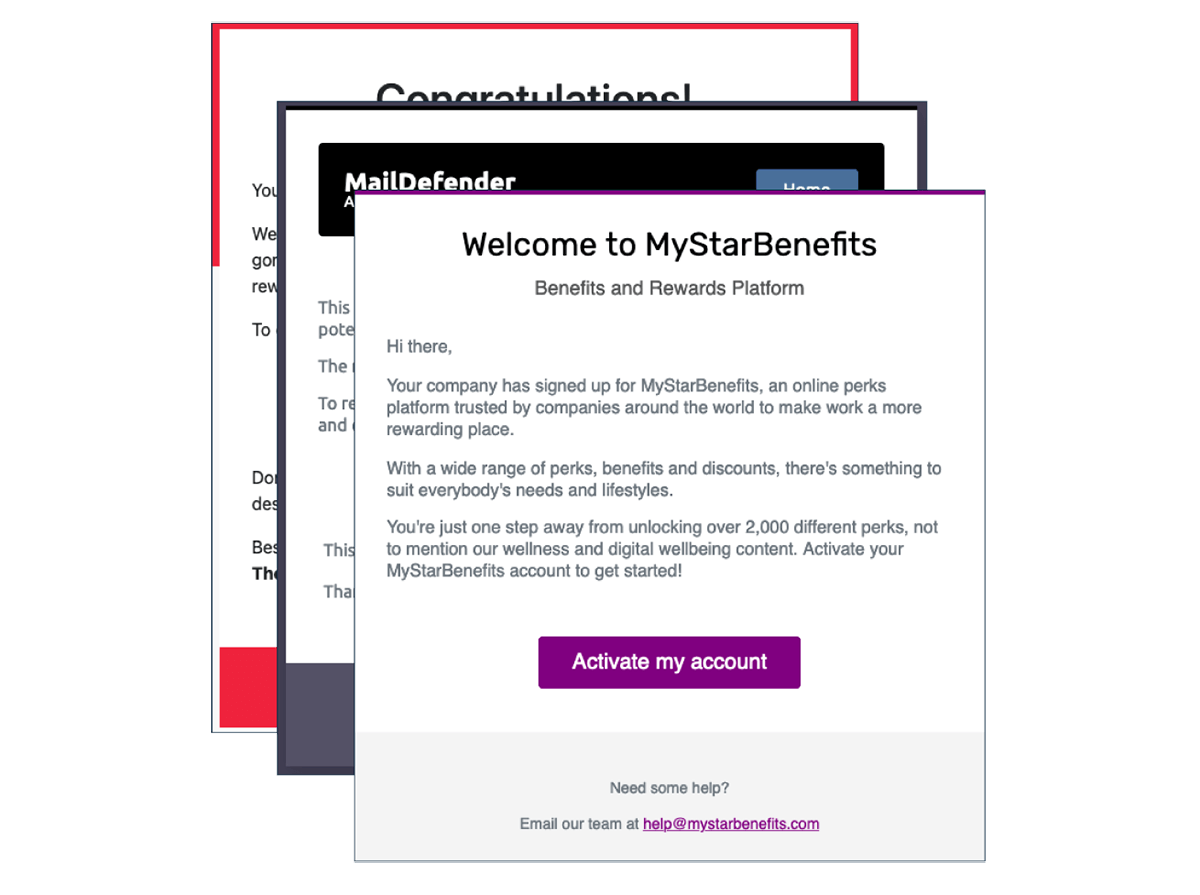
Choose from a range of realistic pre-made templates tailored for each department, designed to create relevant tests that lure your staff into visiting fake websites and entering their credentials.
With a simple 4-step process – select a template, choose who to target, schedule, and confirm – you can get your phishing simulations up and running in minutes.
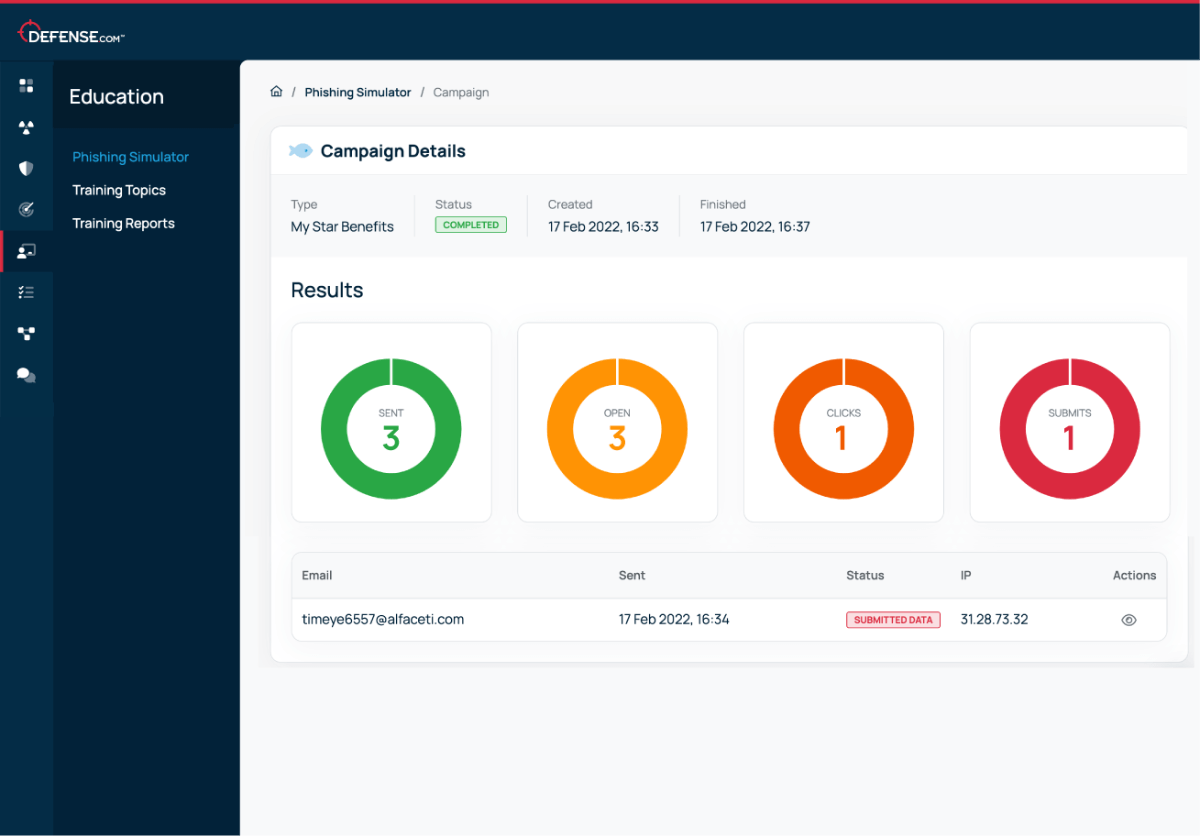
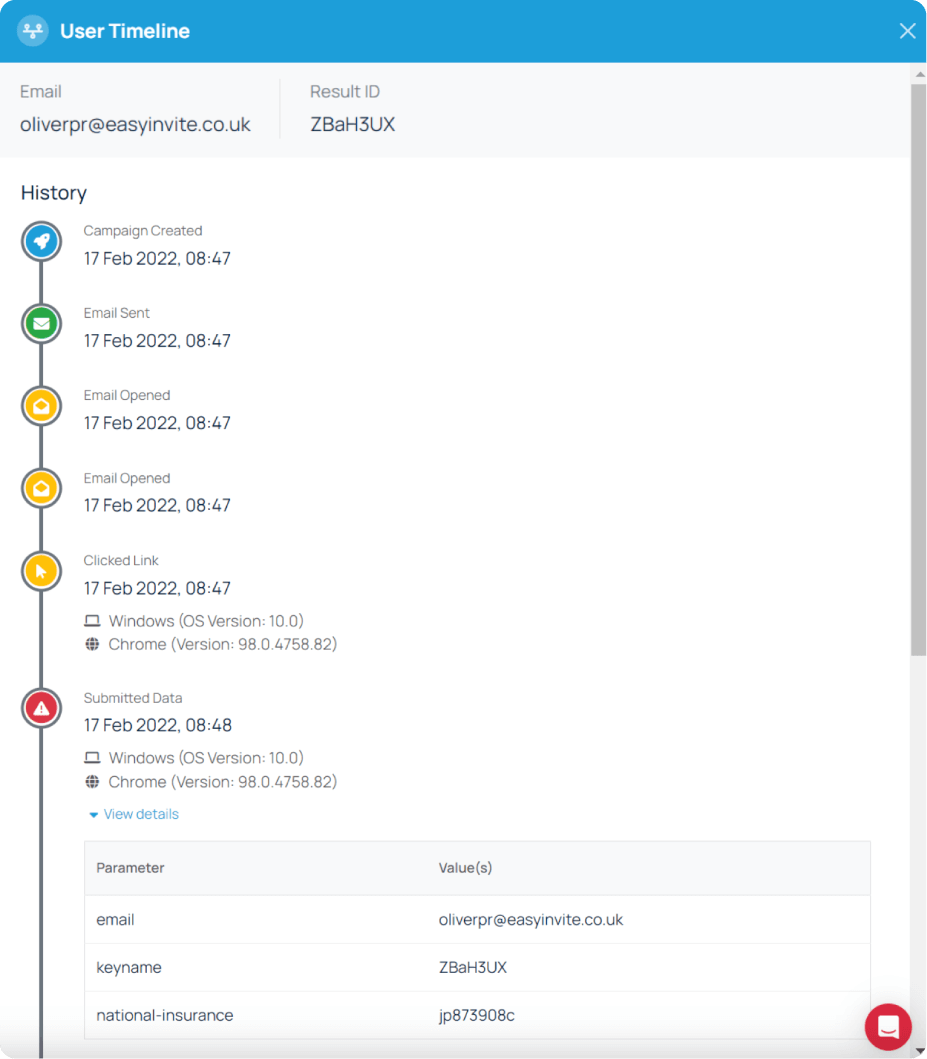
Gain insights with a detailed campaign timeline that tracks user interactions, showing who opened emails, clicked on phishing links, or entered their credentials.
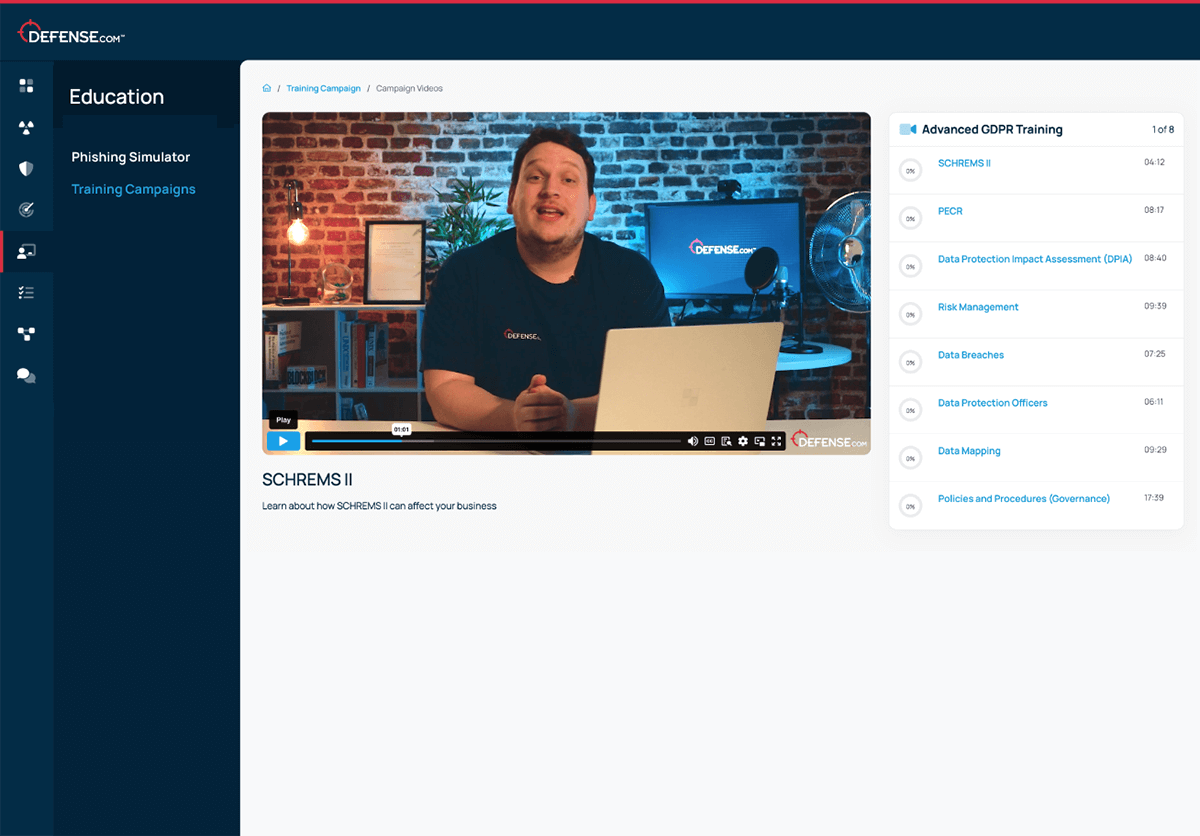
Re-educate staff who fail the phishing simulation using our Security Awareness Training videos.



We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

You can send or schedule as many different phishing campaigns as you like. The only limitation is the number of users that you have added to your Defense.com account.
With Defense.com you can choose from a range of pre-made email templates that link to a dedicated landing page. Each landing page is branded as a fake company and contains a form that is designed to capture information. You can track if any users clicked the email or submitted data in the form, and follow up with individuals to provide further training.
To ensure that your phishing campaigns get delivered successfully, we’d advise whitelisting our domain in your spam filters. Check out this help guide for more information.
Campaigns can run anywhere from a week to a month. We recommend a minimum of two weeks for best results, and for optimal engagement, it's best to schedule the start date on a weekday.
You can target specific departments or groups within your organisation using our pre-made phishing templates. This allows you to customise simulations based on the unique needs and roles of different teams. For example, you can choose templates that reflect the types of emails commonly received by sales, finance, or IT departments, making the simulations more relevant and effective. This targeted approach helps to ensure that each group receives training that is applicable to their daily responsibilities, ultimately enhancing your organisation’s overall security awareness.
Get actionable cyber security advice and insights straight to your inbox.