Product Update – Threat Management
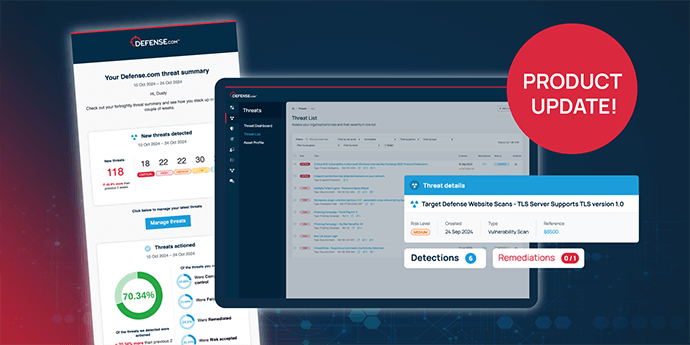
Our enhanced notification system introduces bi-weekly threat digests, intelligent de-duplication, and streamlined alert management, giving your better control and visibility over your security environment.…

Daniel Sampson
Head of Customer Operations
3rd Dec 2024
This month, we’ve rolled out important updates designed to help you manage security threats more efficiently and precisely. These updates focus on improving breach monitoring, refining suppression controls, and expanding the ability to assign remediation tasks across your team. Here’s a closer look at the new features deployed this month.
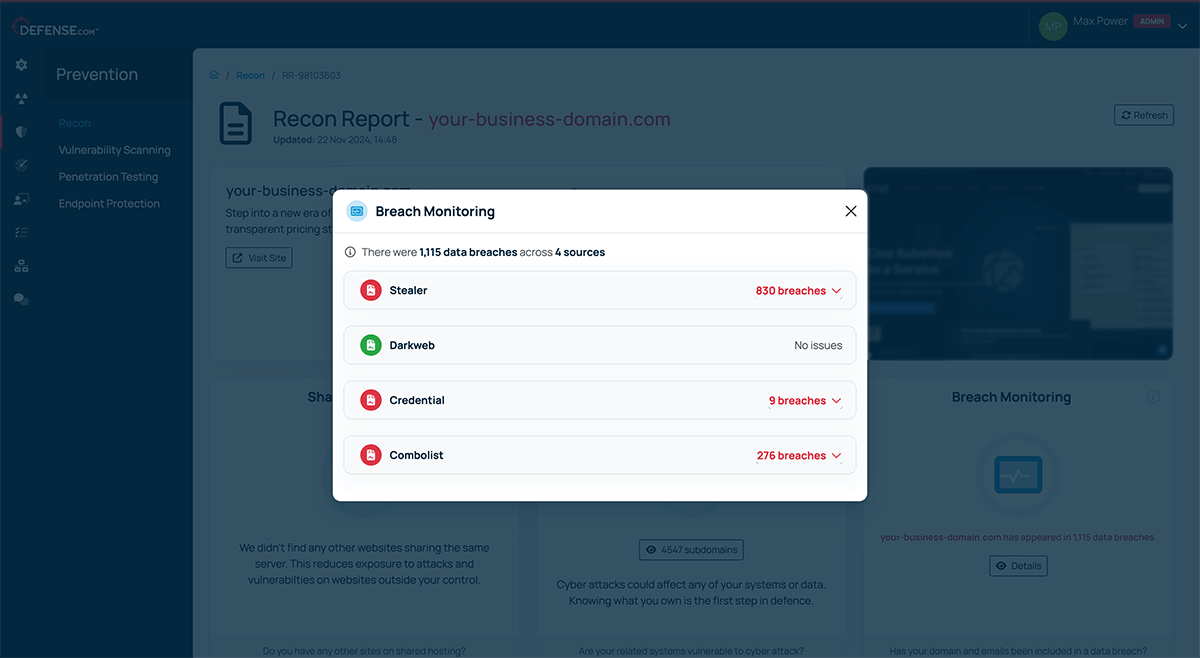
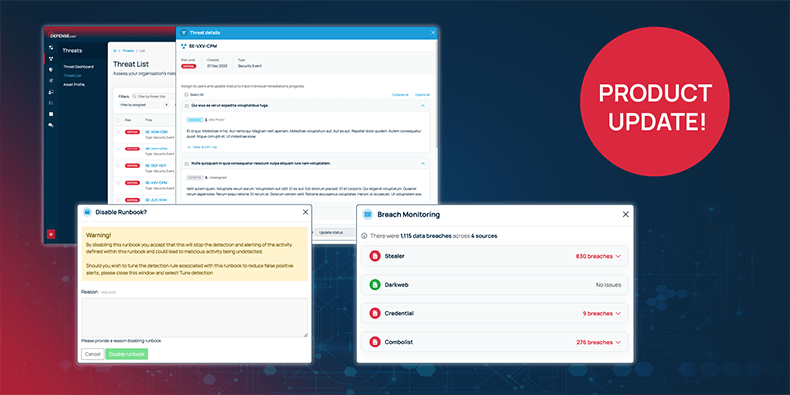
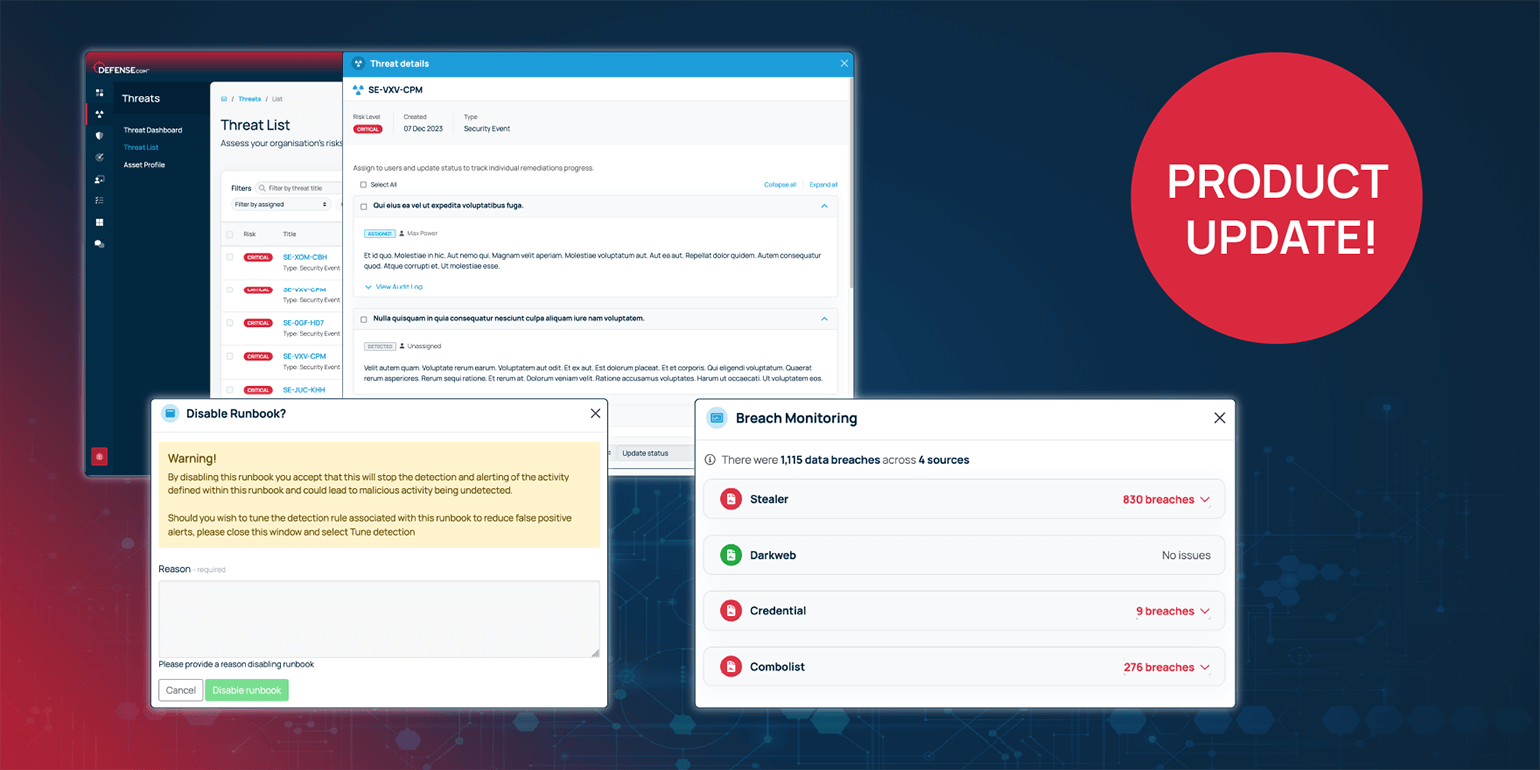
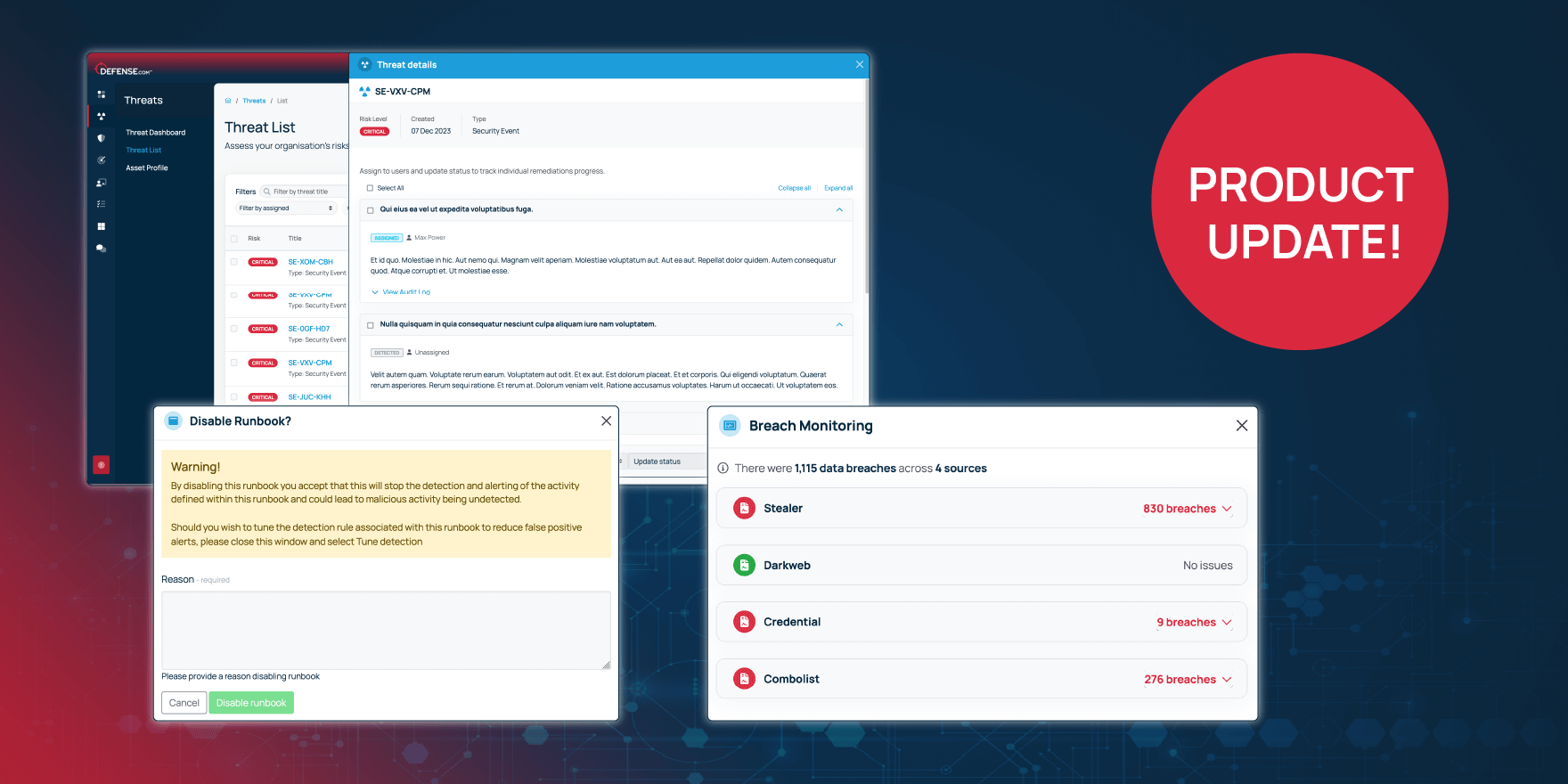
Our dark web recon feature now includes expanded breach monitoring capabilities, giving you deeper insights into potential threats. You’ll receive detailed reports on exposed credentials related to your domain, with the ability to assess whether these passwords are still in active use. Breaches are categorised by their sources including stealer, dark web, credential dumps and combo lists, helping you understand where the exposed data originated. This gives you valuable context on how the breaches occurred and their potential impact on your business.
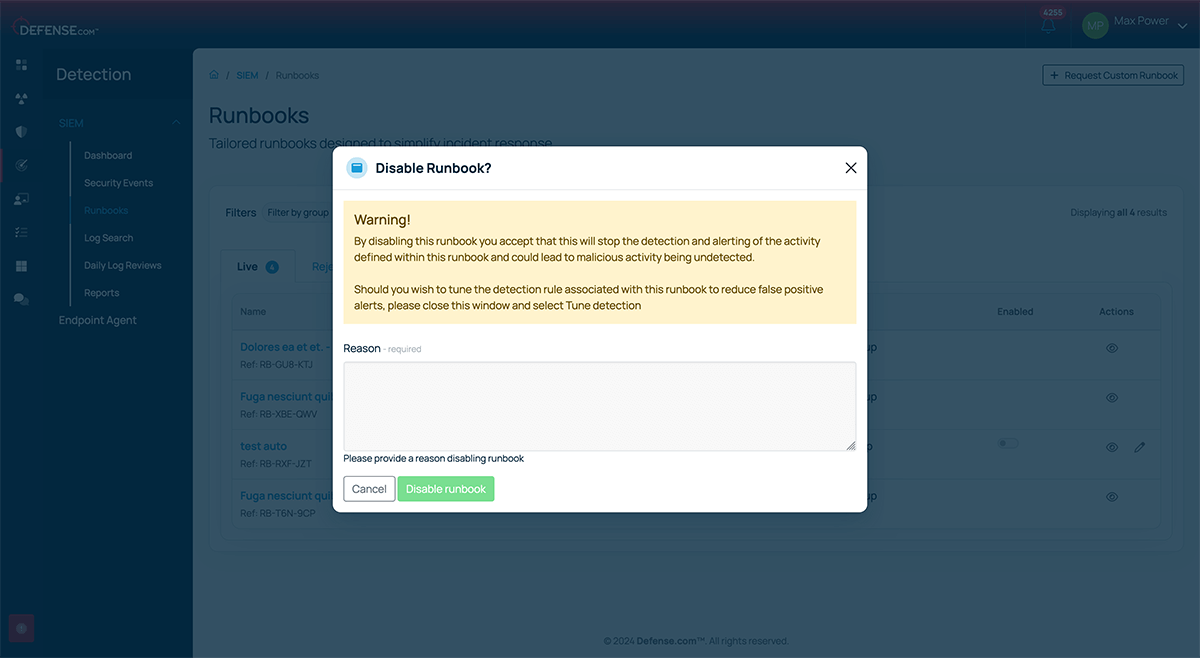
Managing the volume of alerts your team receives is an ongoing challenge. We’ve enhanced our SIEM suppression capabilities to help you cut down on unnecessary noise and let you focus on key events.
Full suppression: You can now fully suppress specific detection rules by switching off entire runbooks. This feature allows you to deactivate noisy alerts, such as those linked to routine activities, without impacting your overall security posture. However, switching off a runbook needs justification, making sure it’s a deliberate action rather than a reactive decision.
Part suppression: For more granular control, we’ve introduced part suppression, which lets you exclude specific users or certain data from triggering alerts. For example, if an admin is repeatedly performing regular tasks, you can suppress alerts related to their activity. This ensures you only receive notifications about genuine unusual or high-risk events, reducing the strain on your security team while maintaining visibility.
These features let you customise your detection system to fit your environment, ensuring you receive the right alerts at the right time while minimising false positives.
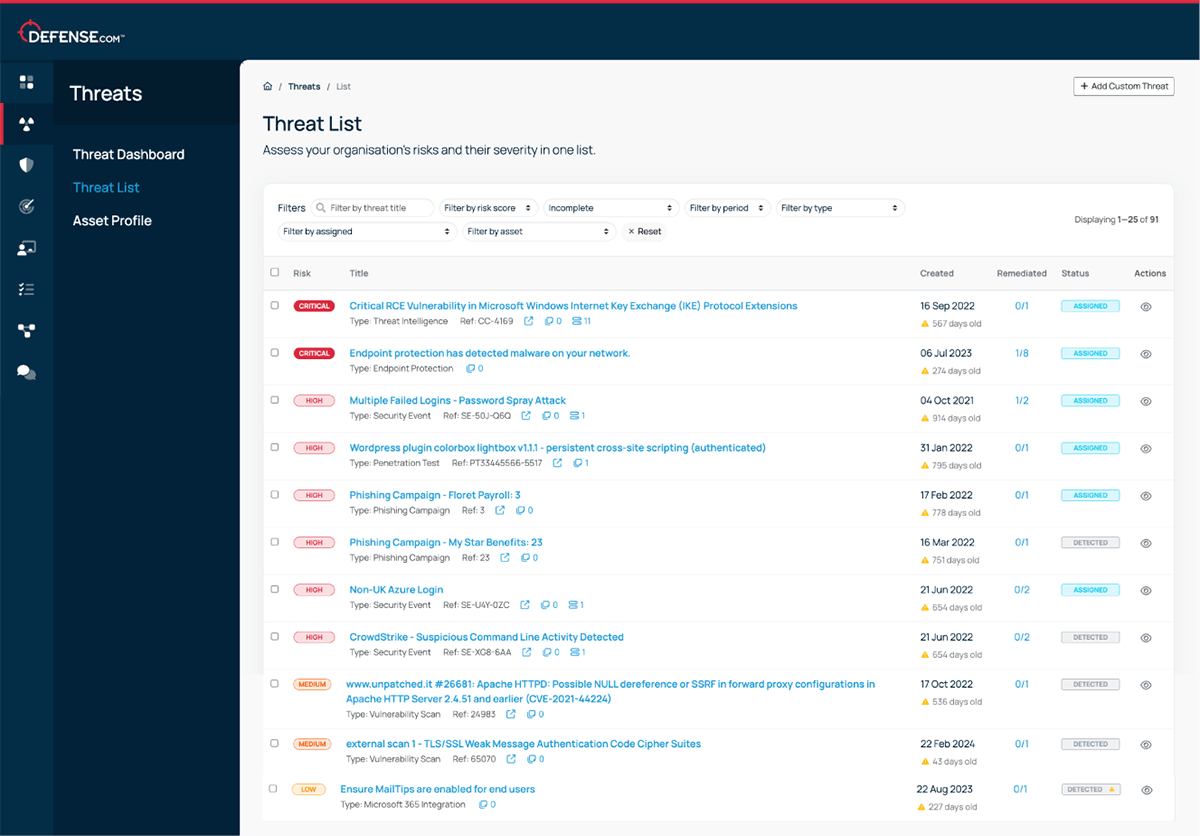
And the final enhancement in this release is the ability to assign threats to standard users.
Previously, remediation tasks could only be assigned to admin users, but now team members, regardless of their role, can directly manage specific threats within the platform.
For example, if an unusual login is detected from a new location, you can assign the threat to the person to validate. This speeds up responses and keeps admins from being overwhelmed by routine checks. The assigned user can add notes, update the status, and track progress, making the process smoother and improves team collaboration.
This month’s updates give you more control over security operations. With better breach monitoring, new suppression features, and the ability to assign tasks to any user, you’ll stay ahead of threats and cut out unnecessary noise. These changes help your team focus on high-priority threats while keeping full visibility across your environment.

Daniel Sampson
Head of Customer Operations
Share this article
Our updated features are available as part of our 28-day free trial. Ready to experience smarter threat management? Try it for yourself today.

Our enhanced notification system introduces bi-weekly threat digests, intelligent de-duplication, and streamlined alert management, giving your better control and visibility over your security environment.…
Our updated phishing simulator offers new templates, easy setup, and custom learning paths, enhancing functionality for better visibility and control over your team’s cyber awareness.…

Find out how you can integrate your Microsoft 365 account with Defense.com to get alerted to new threats, improve your Secure Score and get tailored security advice.…

Discussing the benefits of a security operations centre (SOC), the complexities of building a SOC in-house and 5 reasons why business should outsource their SOC.…
Get actionable cyber security advice and insights straight to your inbox.